Posted
As cybersecurity evolves – so do the tools designed to combat recurring problems that exist within. EDR replaced antivirus. MFA displaced passwords. XDR is basically SIEM dressed to impress. RBAC matured into PBAC/ABAC, and so on.
Still, despite the tremendous progress with available security tools, today’s CISOs face increasing pressures to deliver clear and defensible answers to some seemingly simple questions:
Where is our risk exposure, and what does that mean for the business?
To help find answers, security leaders are leaning more into Cyber Risk Quantification (CRQ). [Quick refresher for those less familiar with the category: CRQ is the process of measuring the financial impact of cyber threats on an organization using data-driven metrics (often dollars)]. But measuring risk, while interesting, can’t be just an academic exercise. CRQ must be used to prioritize risks across the organization – and for everyone from the CISO to the application owner. The approach needs to empower and enable organizations to leverage enterprise-specific threat intelligence while automating and improving risk-informed operational decisions.
Why Traditional CRQ Falls Short: The Case for Threat Intelligence
Traditional risk models frequently take a tech-centric approach, focusing on assets, vulnerabilities, and controls in isolation. While important, these data points often lack context specific to the adversaries (e.g. how they might attack your company). This gap results in critical unanswered questions such as: Which threats are we most exposed to today – what would an attack cost us – how likely is it to happen to us – and – where should we prioritize our budgets to maximize risk reduction?
CRQ only becomes useful when it’s operational, from the boardroom down to the byte.
At ThreatConnect, we believe that CRQ must be operational. It’s not about academic models but about enabling teams to contextualize adversary behavior, prioritize defenses based on financial impact, and take swift action where it matters most.
That’s why ThreatConnect’s Risk Quantifier (RQ) pairs financial risk modeling with live threat intelligence and MITRE ATT&CK. Instead of relying on generic assumptions, RQ reflects how real attackers would operate against your environment, and what those actions would cost.
Transforming Risk Management: The Impact of MITRE ATT&CK Mapping on Unifying Risk
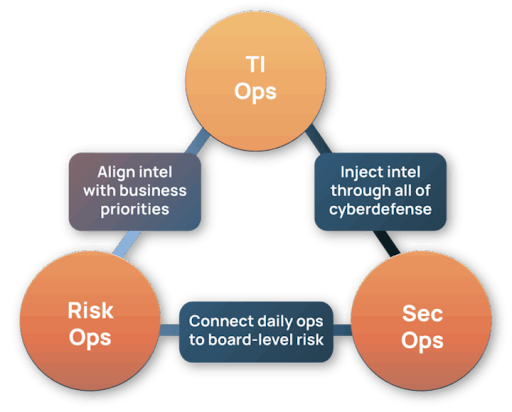
Threat Intel as more than an overlay.
Threat intel is another key element for operationalizing CRQ: without it, CRQ tools revert to theoretical guesswork and produce assessments that are outdated the moment they’re published.
As Paul Kelly, Managing Director at LSEG, puts it:
“CTI is…a key component of CRQ…[It] helps deliver a much more nuanced risk profile, which reflects the exact nature of the risks the businesses face. Achieving this…enables a more business-specific and efficient response to risk as well as gives the CISO confidence that what [they] are presenting to the board is an accurate rather than generic reflection of the business’s position.”
ThreatConnect builds that nuance in by design, pairing financial modeling with evolving threat context to deliver specific, defensible, data-driven guidance.
MITRE ATT&CK – the lingua franca of cyber defense
By aligning CRQ outputs to ATT&CK techniques, ThreatConnect enables CISOs and analysts to speak the same language – from attacker behavior to financial impact. That means Boards see dollars, Analysts see TTPs, and both sides agree on what matters most.
- Prioritize vulnerabilities based on financial risk, exploitability, and threat activity
- Map MITRE techniques to your current defensive coverage and gaps
- Simulate attack paths to model the likelihood and cost of success
- Recommend mitigations with quantified ROI in dollars saved
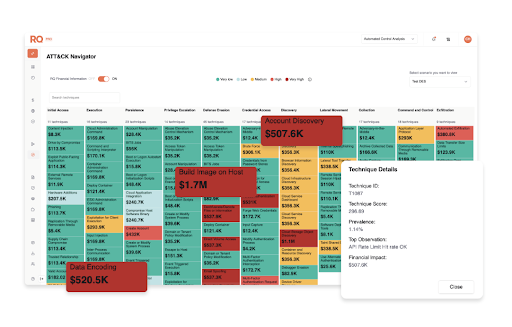
The Transformative Power of ThreatConnect RQ
At the end of the day, threat-informed, financially grounded risk quantification serves as the essential bridge connecting the technical realities of cybersecurity with the strategic imperatives of the business. It dismantles silos by providing a common framework for understanding, prioritizing, and communicating cyber risk that resonates with both security practitioners and business leaders. This unified perspective ensures that security efforts are not just technically sound, but also strategically aligned with the organization’s financial goals, enabling a more cohesive and impactful approach to enterprise-wide risk management.
TC RQ isn’t just about scoring risk; it’s about scaling action. When a cyber risk tool ingests vulnerability data and combines it with business asset data and vulnerability intelligence, your organization can prioritize vulnerability remediation based on financial risk to the enterprise. Specifically,
TC RQ allows customers to:
- Model risk manually, semi-automatically, or fully automatically
- Align threat hunting with business priorities
- Quantify the cost of control gaps and justify mitigations in plain dollars
Resulting in a customer value chain that includes:
- Scenario modeling that drills into specific MITRE techniques
- Transparent business impact assessments
- A defensible connection between cyber risk and financial exposure
Together with our TIP, ThreatConnect strengthens the connection between threat intelligence and risk teams, providing a holistic, financially driven approach to cyber risk management.
Closing the Exposure Gap
TC RQ doesn’t just sit on a shelf. It drives defense at every level of the organization.
By combining high-fidelity threat intelligence with the MITRE ATT&CK framework, TC RQ enables risk leaders by calculating the financial impact a cyber attack could have based on a defined set of MITRE ATT&CK capabilities and a company’s Defensive Posture. This data allows users to see their gaps in coverage using financial analysis and prioritize based on financial risk reduction, eliminating wasted effort on low-impact scenarios and focusing on what’s truly material to the business.
Without the powerful combination of CRQ + Threat Intel, CRQ solutions are plagued by significant blind spots, including mis-prioritized vulnerabilities, generic risk assessments, and the ability to powerfully encapsulate how something like the MITRE ATT&CK framework helps bridge the gap between technical attacker behavior and financial impact.
Your final takeaway? CRQ leaders should emphasize the importance of choosing a solution that automates and enhances risk-informed operational decisions.
ThreatConnect RQ is designed for exactly that. Ready to see ThreatConnect RQ in action? Sign up now for a personalized demo.