Posted
It began, as many mysteries do, with a statement of defeat.
“There’s no way we could have prevented this.”
Baskerville Bank had just suffered a crippling ransomware attack. Production systems were encrypted. The customer portal was dark for 12 hours. Operational disruptions cost over $3.2M, not counting the inevitable PR fallout, legal action, and suspected data theft.

The bank’s internal investigators had a hunch it started with an exploited help desk plugin. But they didn’t know how the attacker got in, and they were convinced prevention was impossible.
They were wrong.
ACT I – A Cyberattack Most Foul
When Threatlock Holmes took the case, the picture sharpened immediately.
- Initial access: A phishing spoof of a known fintech partner.
- Early clue: The spoofed domain appeared in multiple intel feeds – three days before the breach.
- Payload: A remote access trojan delivered via a known plugin vulnerability (CVE-2024-30219).
- Tradecraft: TTPs mapped cleanly to Midnight Jackal, a threat actor with recent banking sector activity.
In other words: the domain could have raised alarms. The plugin could have been patched. The actor’s behavior could have been recognized. The clues were all there – just not connected.

ACT II – How a TIP Helps Crack the Case
At its core, a Threat Intelligence Platform (TIP) is an optimization tool that sits between your upstream threat data (intel sources) and your downstream operational tools. It takes in raw, inconsistent data and produces high-fidelity intelligence you can act on.
We think of it as AAA – Aggregate, Analyze, Act.
1. Aggregate – No Clues Left Behind
| Without a TIP | With a TIP |
| Relying on a single feed creates blind spots.
Multiple feeds mean multiple formats, multiple logins, and a high cognitive load. No way to compare timeliness or quality between sources. |
Aggregate OSINT, commercial, internal, and government sources into one Unified Threat Library. Correlate indicators across feeds. Measure feed quality:
|

In Baskerville’s case, a more timely feed had flagged the phishing domain three days early. A TIP would have surfaced that clue before the breach.
2. Analyze – Give Every Clue Context
Without a TIP:
- Indicators are “orphaned” – bad.com is bad, but why?
- No links between observed activity and known actors, campaigns, or CVEs.
- Investigations stall on isolated data points.
With a TIP:
- Correlate IoCs to MITRE ATT&CK techniques, threat actors, and vulnerabilities.
- Automatically enrich and deduplicate intel.
- Flag related campaigns and active activity.
- Focus on behaviors, not just artifacts.
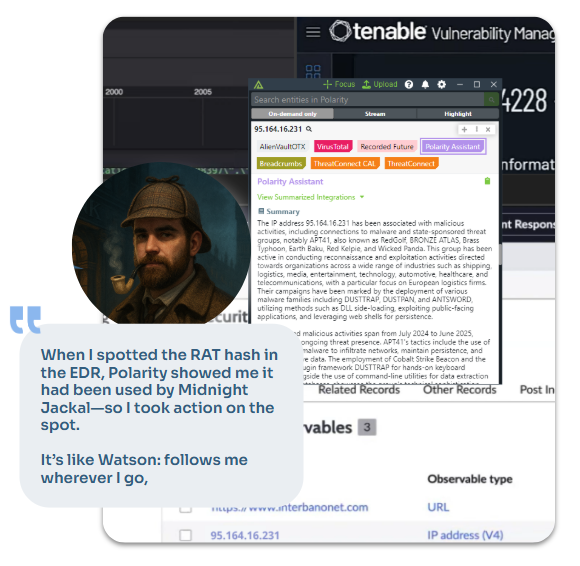
In our example, enriching the RAT hash tied it directly to Midnight Jackal’s known tactics – the same ones exploiting the vulnerable plugin.
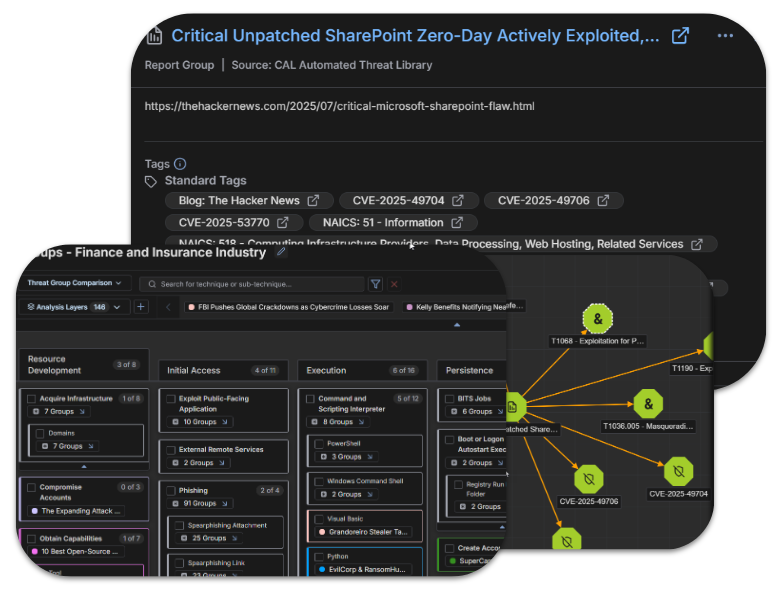
3. Act – Get Intel Where It Matters, When It Matters
Without a TIP:
- Intel gets stuck in PDFs or spreadsheets.
- Sharing is manual and delayed.
- Indicators are piped directly into SIEMs, causing alert overload.
- Strategic reporting is inconsistent.
With a TIP:
- Technical dissemination – Push high-fidelity IoCs to SIEMs, EDRs, SOARs, firewalls.
- Strategic dissemination – Produce role-specific reports for SOC, CTI, risk, and executives.
- Gather feedback to continuously improve relevance.
For Holmes, this meant pushing the RAT hash to the SIEM immediately – days before the attack.
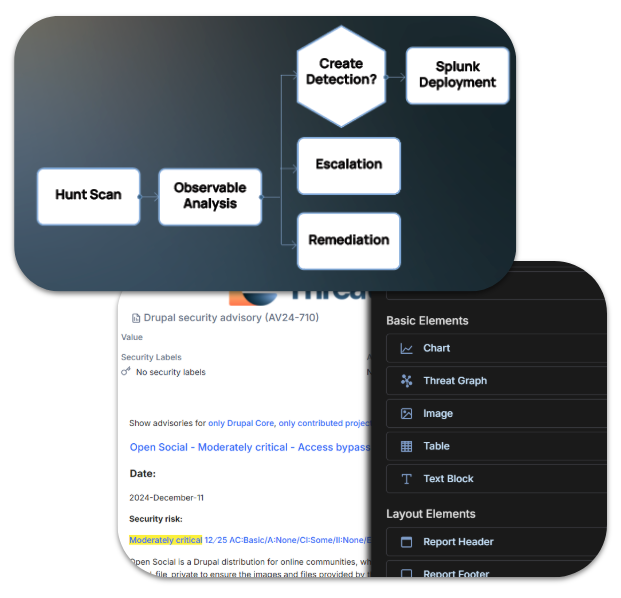
ACT III – Modern TIP Use Cases
A TIP isn’t just about the basics anymore. Here’s what separates a modern platform from a legacy intel repository.
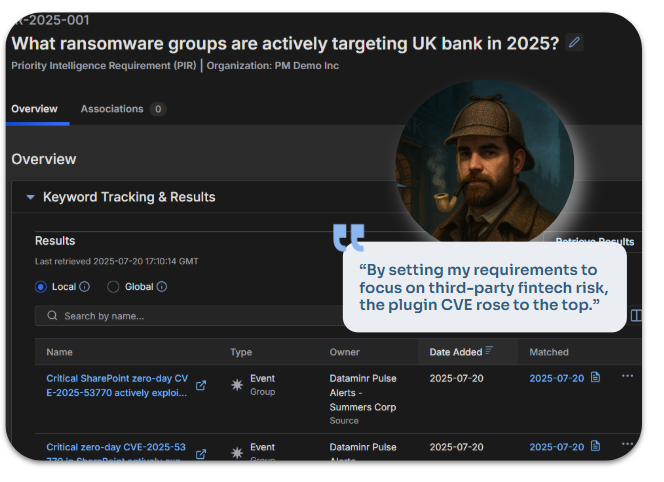
Intelligence Requirements – Filtering the Noise
Mature teams start by defining Priority Intelligence Requirements (PIRs) with stakeholders – increasingly with business and executive input. This ensures intel collection aligns to real business risk.
In ThreatConnect’s TI Ops platform, you can enter a plain-English PIR (“Which ransomware groups are targeting UK banks this year?”). AI turns it into keywords, classifies unstructured reports, and continuously pulls relevant intel from across your sources.
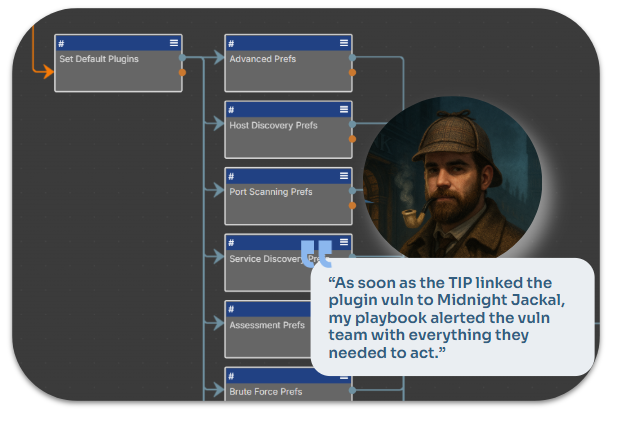
Background Automation – Freeing Analysts for Real Work
The goal isn’t a “lights-out SOC.” It’s removing the cut-and-paste drudgery so analysts can focus on high-impact threats.
Look for:
- Multithreading – Handle tens of thousands of automated tasks daily.
- Flexibility – Connect to your existing tech stack, not the other way around.
In our case, once the vulnerability was linked to Midnight Jackal, an automation playbook alerted the vulnerability team with all required context.
Business-Aligned Threat Modeling – Speaking the Board’s Language
Defenders often model threats by frequency. The business cares about financial impact.
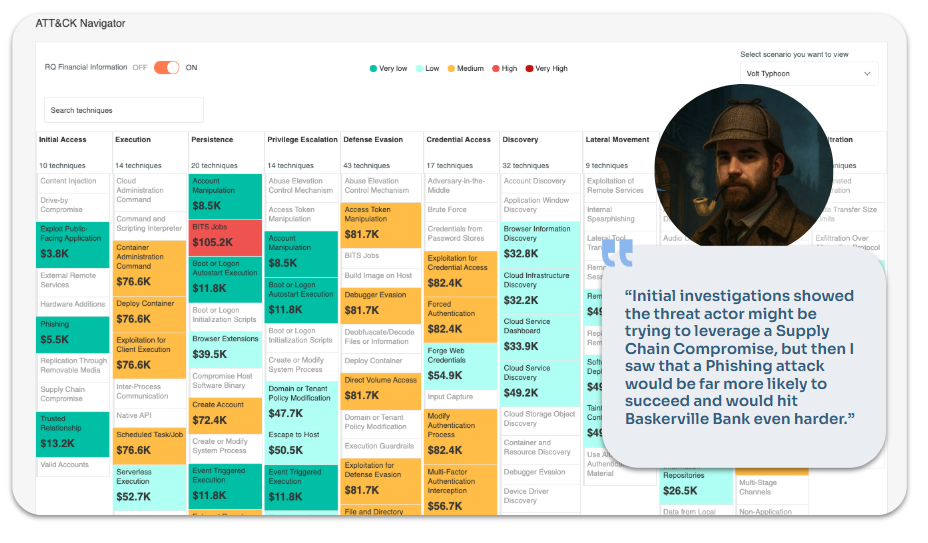
ThreatConnect’s Risk Quantifier (RQ) and TI Ops maps TTPs to dollar values based on breach history, your assets, and your controls. In Baskerville’s case, phishing – the most common TTP – represented just $5.5K in risk, while “bits jobs” posed a $105K exposure.
This reframes priorities, enabling better resource allocation – and better budget justification.
In-Your-Face Dissemination – Intel Without Context Switching
Even the best intel fails if it’s not in front of the right person at the right time.
Polarity by ThreatConnect is an overlay that works in any tool – SIEM, EDR, ticketing, vuln manager – with no integration required. Highlight an indicator, and it federates search across all your intel and operational systems, summarizes results with AI, and lets you take action instantly.
For small teams wearing many hats, this can be the difference between catching a threat in seconds versus hours.
ACT IV – Closing the Case
Threatlock Holmes’ method wasn’t magic. It was disciplined, repeatable tradecraft – supercharged by the right platform.
He:
- Set proper intelligence requirements aligned to business risk.
- Focused investigation on the highest-impact threats.
- Automated repetitive tasks to keep his intellect free for analysis.
- Aggregated multiple feeds to avoid blind spots.
- Contextualized IoCs by linking them to actors, TTPs, and vulnerabilities.
- Integrated his SIEM with high-fidelity intel from a Unified Threat Library.
- Disseminated intel directly to the point of action via overlay.

Can Your Team Solve the Next Case?
Ask yourself:
- Are you aggregating intel across all your sources?
- Do your analysts know exactly what to prioritize?
- Can you act from within your existing tools?
- Can SOC, CTI, IR, and risk teams all see the same threat, the same way?
If not, you may be missing your own Midnight Jackal clues – and leaving the next Baskerville-scale breach preventable, but unprevented.
Your move, detective.
Book a demo to see a modern TIP in action.



