Posted
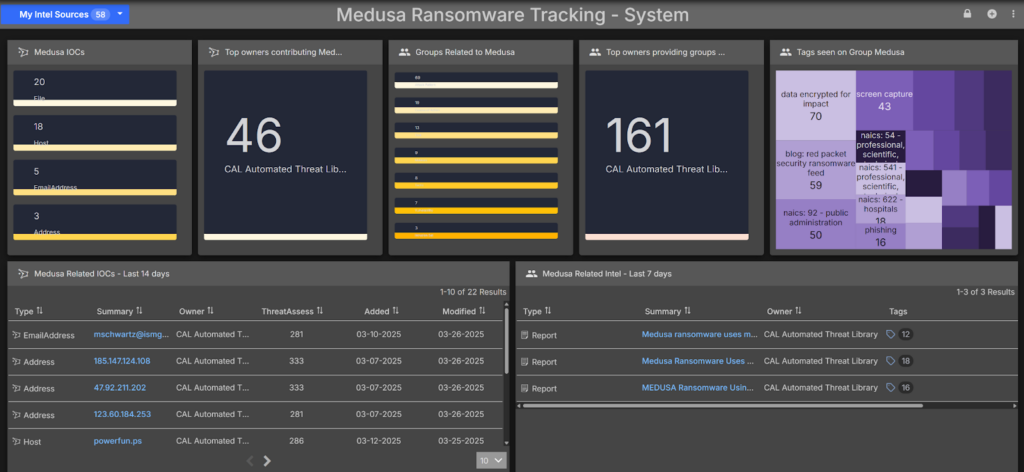
The Medusa Ransomware Threat Dashboard in ThreatConnect provides security teams with real-time visibility into the latest activities, indicators, and trends associated with the Medusa ransomware threat group. This dashboard aggregates threat intelligence from multiple sources, enabling analysts to proactively detect, track, and mitigate Medusa-related threats before they impact the organization.
Key Benefits:
- Centralized Intelligence: Consolidates Medusa-specific indicators of compromise (IOCs), tactics, techniques, and procedures (TTPs) from open-source intelligence, threat feeds, and internal telemetry.
- Real-Time Threat Tracking: Provides up-to-date alerts on Medusa’s evolving attack patterns, newly discovered vulnerabilities, and victim profiles.
- Incident Response Acceleration: Enables rapid threat triage and response by offering enriched intelligence and contextual analysis.
- Customizable Reporting & Visualization: Delivers interactive charts, trend analysis, and case studies on Medusa ransomware campaigns to support executive and operational decision-making; and
- For customers interconnected to defensive technologies — Automated Correlation: Uses ThreatConnect’s intelligence-driven automation to find Medusa-related IOCs associated with adversaries, reports, and intrusion sets to help prioritize potential threats and take appropriate action.
By leveraging the Medusa Ransomware Threat Dashboard, security teams can enhance their threat intelligence capabilities, reduce response times, and strengthen their organization’s resilience against ransomware attacks.
Lead Contributor – Angel Salcedo, Customer Success Engineer
To gain access to the Medusa Ransomware Threat Dashboard, please reach out to your Customer Success team or email us at customersuccess@threatconnect.com.
What Is Medusa Ransomware?
Medusa Ransomware is a ransomware-as-a-service (RaaS) variant first identified in June 2021, targeting organizations across various critical infrastructure sectors. It encrypts victims’ files and demands a ransom for decryption, with affiliates using tactics like phishing, remote desktop protocol (RDP) exploitation, and unpatched vulnerabilities to gain access. As of February 2025, over 300 organizations have been affected. To mitigate risks, CISA recommends regular software updates, network segmentation, and traffic filtering. More details on indicators of compromise (IOCs) and defensive measures are available in the full advisory.
Further Resources
For more detailed information and resources on Medusa, please refer to the following:
| Resource | Description | Link |
| CISA Alerts | Provides timely information about current cybersecurity threats and vulnerabilities | https://www.cisa.gov/news-events/cybersecurity-advisories/aa25-071a |
We urge all organizations to remain vigilant and proactive in their cybersecurity efforts. By implementing these recommendations, you can significantly reduce your risk and protect your critical assets.

