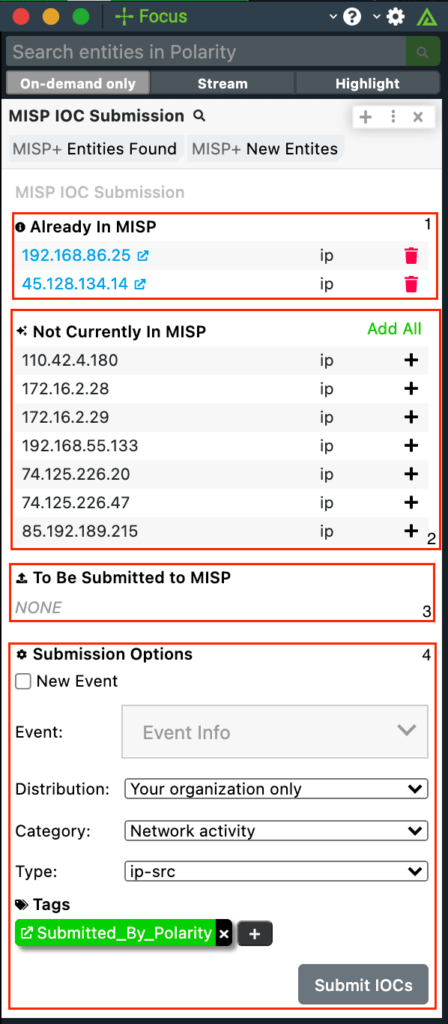
MISP
A threat intelligence platform for sharing, storing and correlating Indicators of Compromise of targeted attacks, threat intelligence, financial fraud information, vulnerability information or even counter-terrorism information.
Integrations
Related Resources
Built By ThreatConnect
Related Resources
Built By Polarity
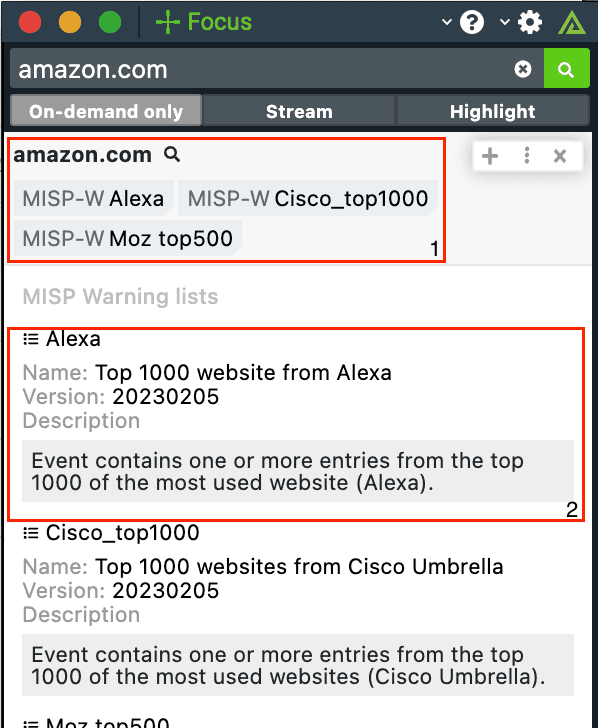
MISP Warning Lists with Polarity
Keep ReadingRelated Resources
Built By Polarity


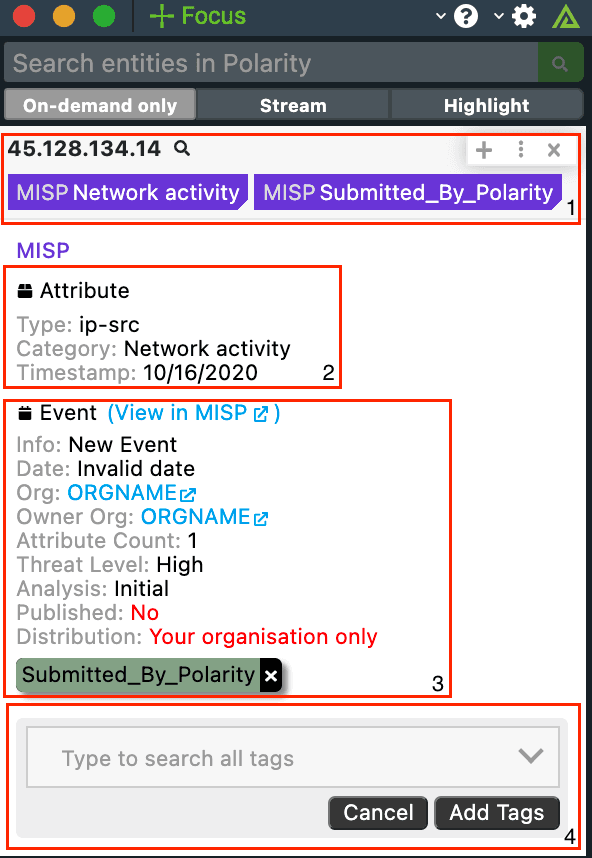
 Polarity
Polarity