AI-Driven Intelligence
Deliver real-time insights, rapid analysis, and intelligent dissemination to help defenders stay ahead of evolving threats
Generative AI and Machine Learning for CTI
Real-time, AI-driven insights for high-confidence intelligence that empowers faster decisions while reducing analyst workload.
Key Features:
- Dynamic Threat Detection: AI analytics to identify patterns and emerging risks in real-time, enabling proactive threat mitigation.
- High-Fidelity Insights: Filtering out noise to deliver relevant intelligence, reduce false positives and boost efficiency.
- Trusted Intelligence: AI-driven analysis and crowd-sourced data deliver accurate, actionable insights.
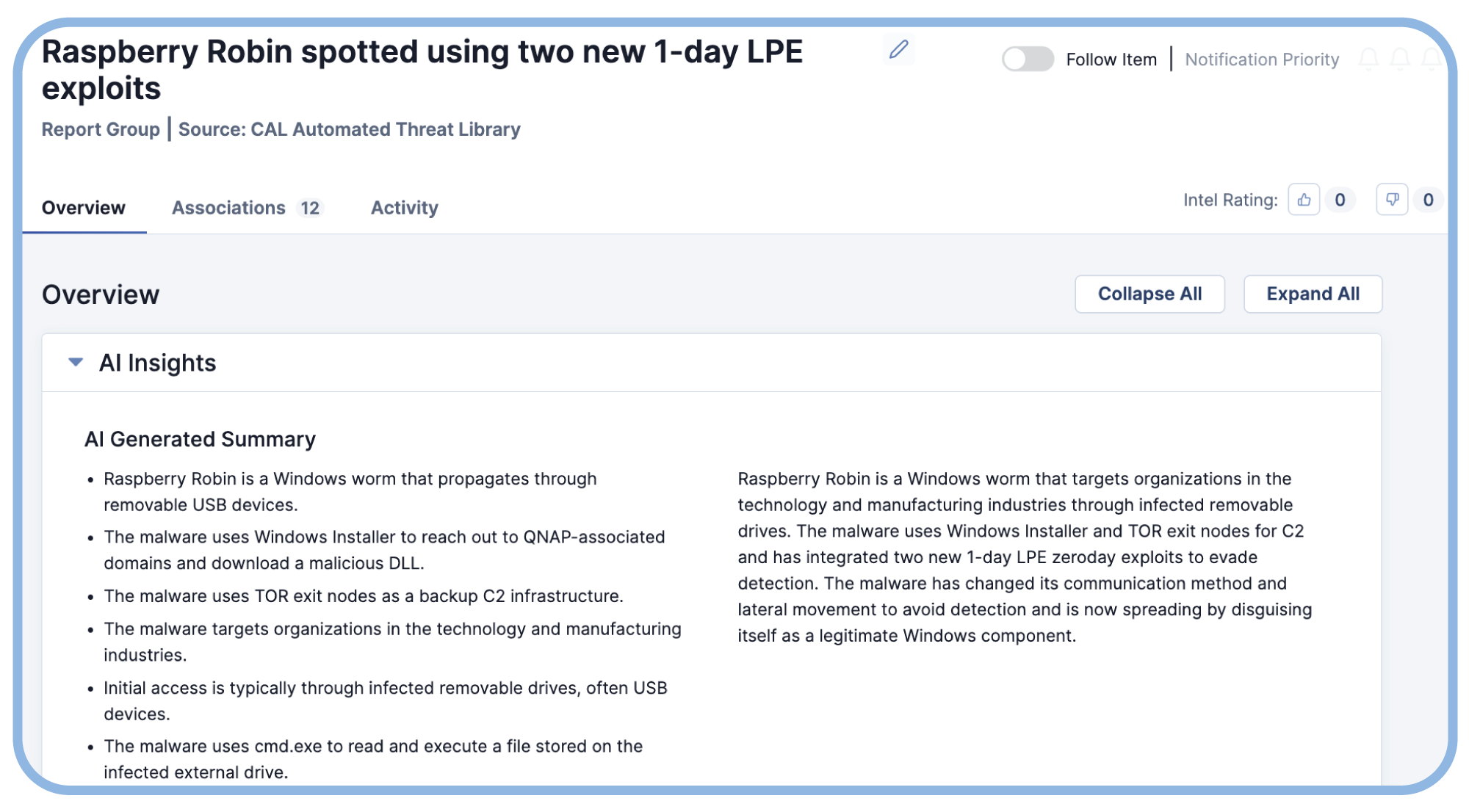
Explore CAL™ — ThreatConnect's AI & ML Engine
Learn MoreFederated Search with AI Summarization
Accelerate intelligence discovery with federated search and AI-powered summarization, enabling analysts to access critical insights faster.
Key Features:
- Federated Search Across Platforms – Unify queries across intelligence repositories and operational systems, delivering a consolidated view and eliminating platform switching.
- AI-Powered Summarization – Distilling large datasets into concise insights to simplifies complex information and help analysts prioritize high-impact intelligence.
- Optimized Workflow Efficiency – Minimize search redundancies, accelerate investigations, and enhance decision-making with clear, actionable intelligence.
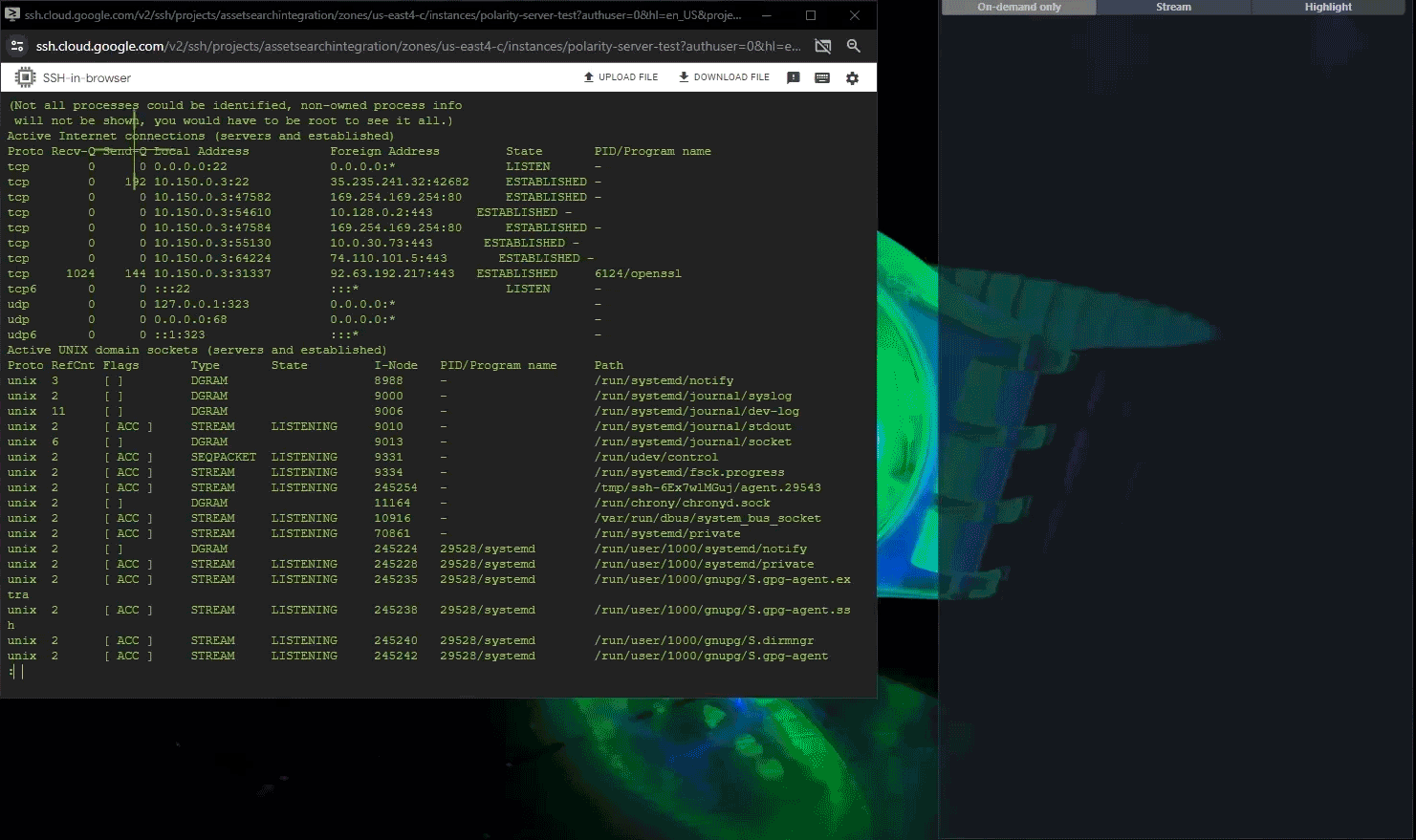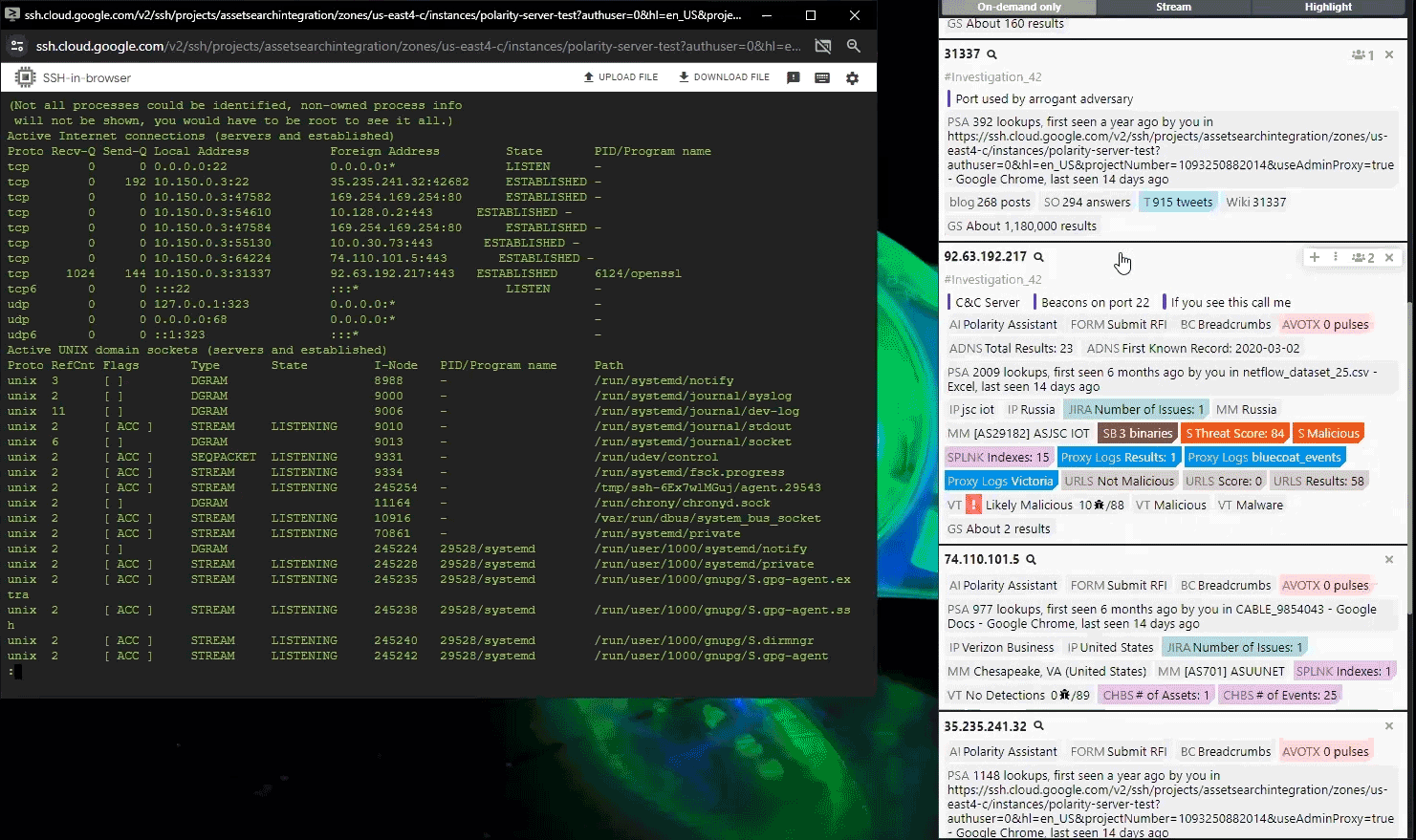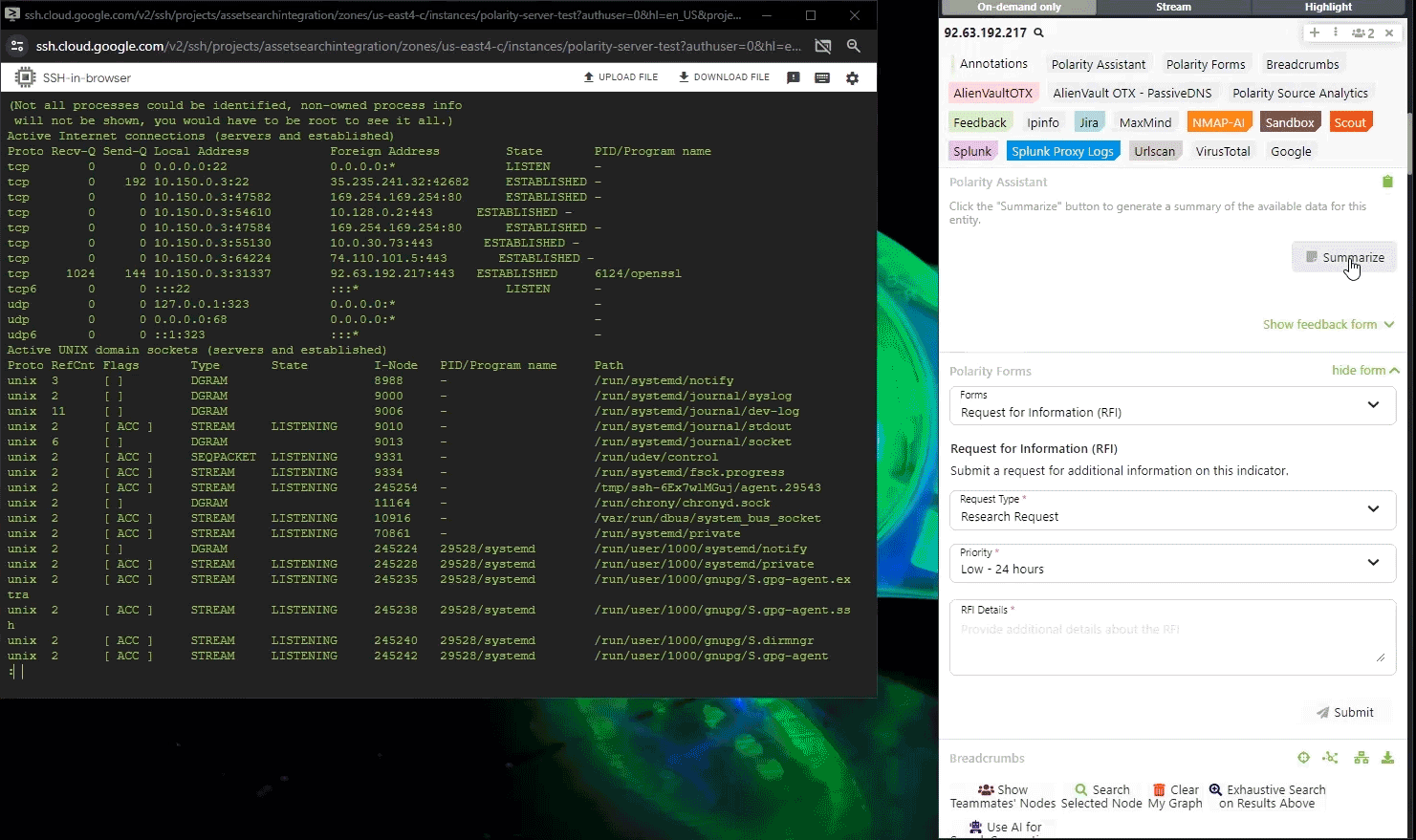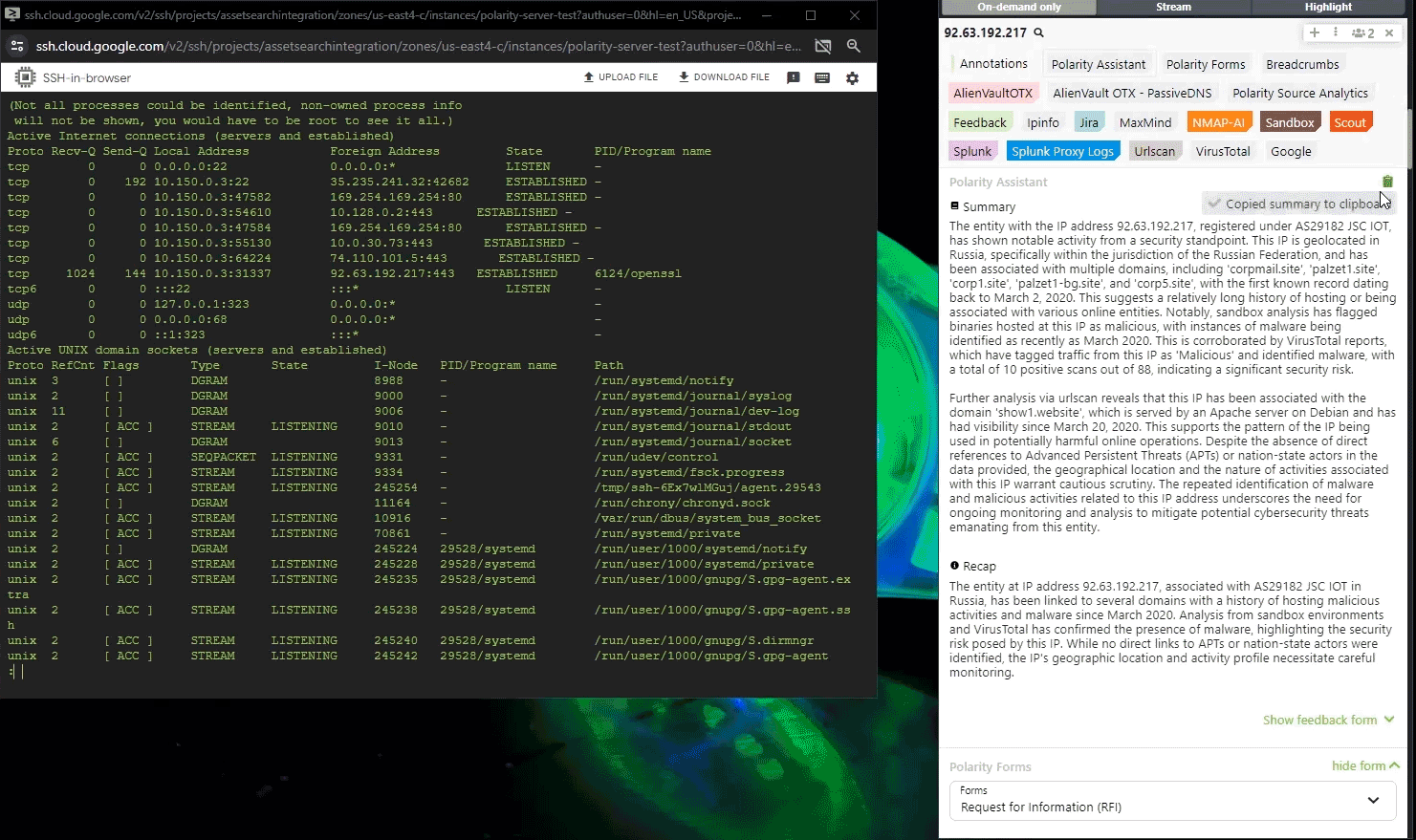
See How Polarity Accelerates Investigations
Take the TourSeamless Intelligence Dissemination
Streamline intelligence sharing with AI-powered summaries and reports, ensuring critical insights reach key decision-makers. Automate reporting to enhance collaboration, improve efficiency, and increase accuracy.
Key Features:
- Streamlined Report Generation – AI automatically compiles concise, detailed reports, transforming vast data into actionable intelligence.
- Collaborative Distribution – Integrate with workflows to deliver intelligence in real time, ensuring the right stakeholders receive timely insights.
- Consistent and Efficient Sharing – Prebuilt reporting templates enable quick, standardized dissemination, enhancing communication across teams.
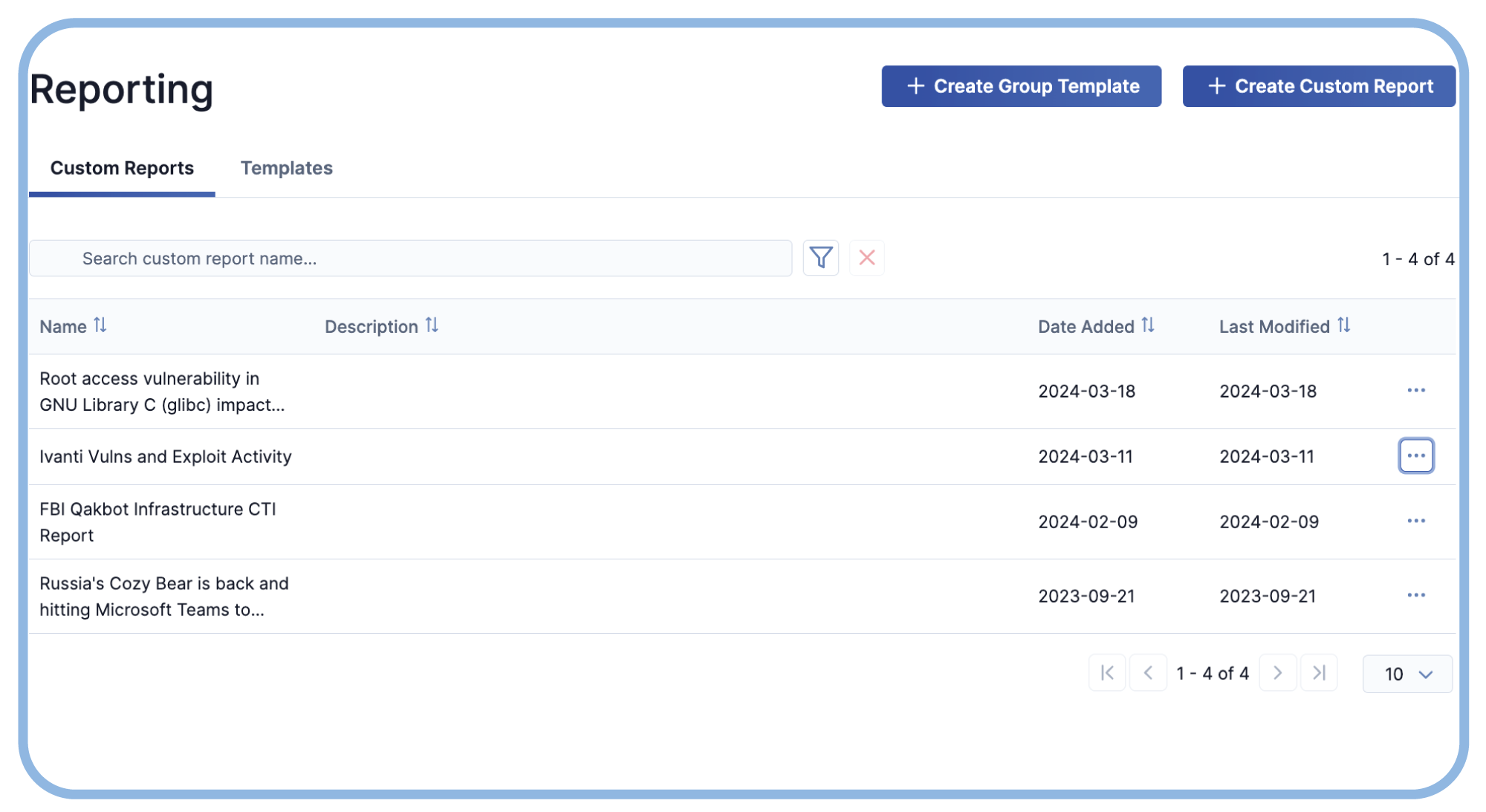
See How ThreatConnect Enhances TI Reporting
Take the TourTransform Intel with AI-Powered Insights
How We Leverage AI
Discover how our threat intelligence platform uses AI to improve decision-making.
Accelerate Investigations with AI Integrations
Access diverse data sets, LLMs, and AI platforms through an intuitive, no-code interface.
Beyond the Buzzword: Real World Applications for AI
Explore real-world use cases, successes, and lessons on balancing AI and human expertise for better security workflows.
