Posted
Phishing remains one of the most effective and pervasive attack methods for cybercriminals, with threats evolving in sophistication and becoming increasingly difficult to detect. To stay ahead, security teams need tools that deliver contextualized intelligence and seamless workflows to tackle these challenges. ThreatConnect and Polarity provide an integrated solution to address phishing threats effectively, empowering analysts to move from detection to resolution with greater speed and precision.
In addition to tackling traditional phishing methods, this blog will also explore how these solutions help address emerging threats, such as the exploitation of QR codes, providing security teams with the tools they need to defend against a wide range of phishing tactics.
Unified Threat Intelligence in Context
ThreatConnect aggregates intelligence from sources like abuseIP, OSINT feeds, and proprietary databases, providing enriched insights into phishing indicators such as domains, IP addresses, and malicious links. Polarity enhances this by overlaying critical intelligence directly within the analyst’s workflows, eliminating the need to toggle between tools. This unified context helps analysts quickly assess risks and prioritize their response.
Streamlined Detection and Enrichment
Phishing thrives on exploiting ambiguity, but ThreatConnect and Polarity bring clarity. Analysts gain instant insights into suspicious elements by enriching artifacts like email headers or embedded URLs with actionable threat intelligence. Polarity further simplifies workflows by presenting this information in real-time, directly where analysts work, ensuring nothing is missed.
Automation Meets Human Insight
ThreatConnect’s playbooks automate repetitive tasks like blocking malicious senders or isolating phishing emails, allowing analysts to focus on higher-value activities. Polarity complements these automations with human-centric overlays, providing analysts with critical context for decision-making and collaboration.
AI and Collective Analytics for Smarter Decisions
Using CAL and Polarity’s AI-driven insights, phishing indicators are cross-referenced with community-driven data and predictive analytics. This helps detect ongoing threats and anticipates future phishing tactics, enabling proactive defense.
Integrated Workflows for Efficiency
ThreatConnect and Polarity integrate with tools like email gateways, SIEMs, and SOAR platforms. This ensures security teams can operate without disruption, leveraging all available intelligence to maximize efficiency and effectiveness.
Polarity’s New QR Code Recognition Feature
QR codes have become ubiquitous, seamlessly blending into our daily lives through mobile payments, restaurant menus, and promotional campaigns. However, their widespread adoption has created an opportunity for threat actors to exploit this seemingly innocuous technology for malicious purposes. Cybercriminals have weaponized QR codes to distribute malware, conduct phishing campaigns, and facilitate other harmful activities, preying on users’ trust and the often-hidden nature of the embedded content.
One common tactic is embedding malicious URLs within QR codes, leading unsuspecting users to phishing sites designed to steal login credentials, financial information, or other sensitive data. Additionally, attackers use QR codes to initiate unauthorized actions, such as downloading malware onto a victim’s device or activating harmful scripts that compromise system security. Even more sophisticated threats involve QR codes disguised as legitimate payment gateways, enabling attackers to reroute transactions to fraudulent accounts.
These risks are further amplified by the challenge of decoding QR codes without specialized tools. Users cannot visually inspect a QR code’s content, making it easy for attackers to hide malicious payloads. Security analysts face the daunting task of identifying and mitigating such threats, often under time-sensitive conditions where every second counts.
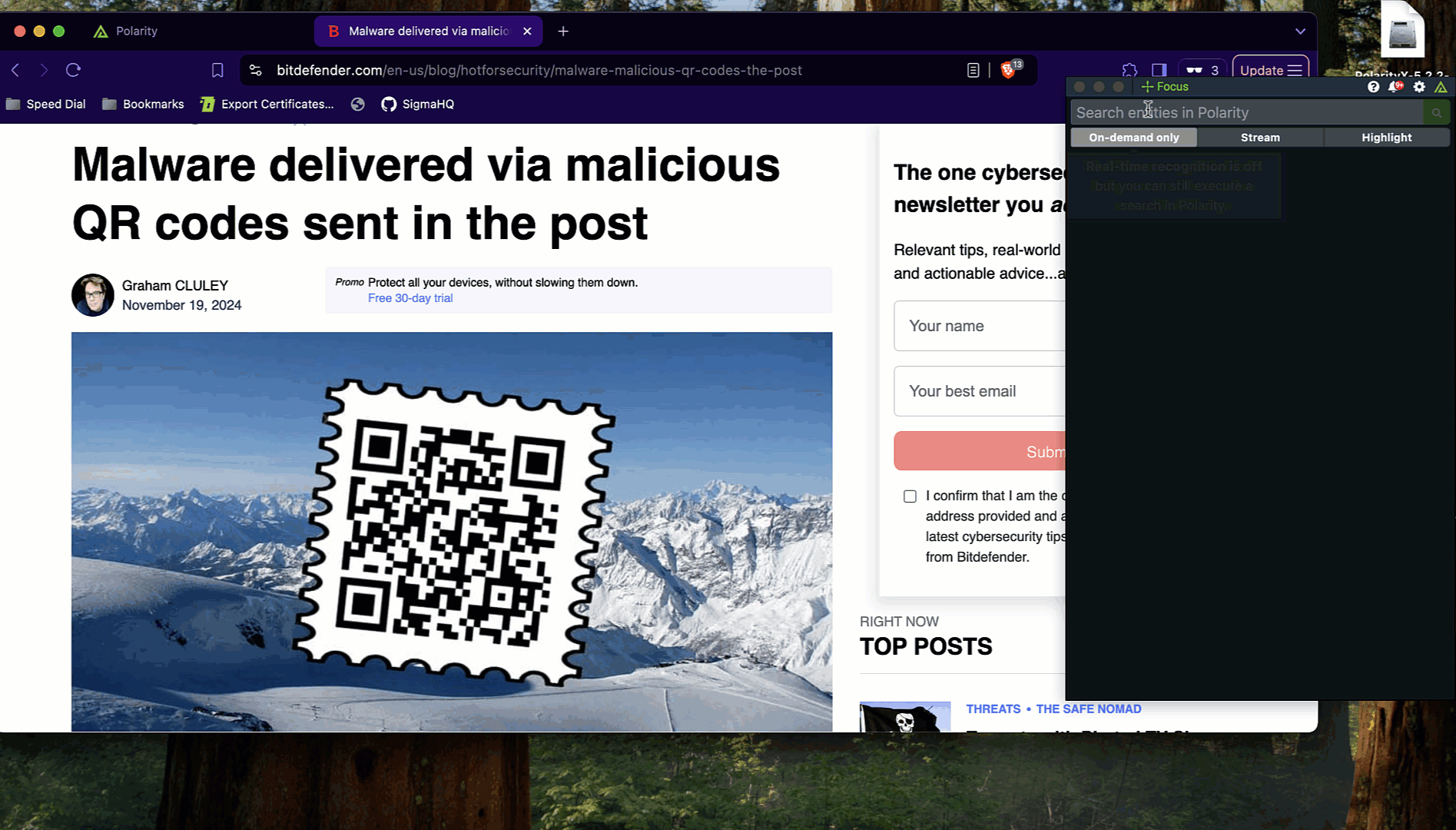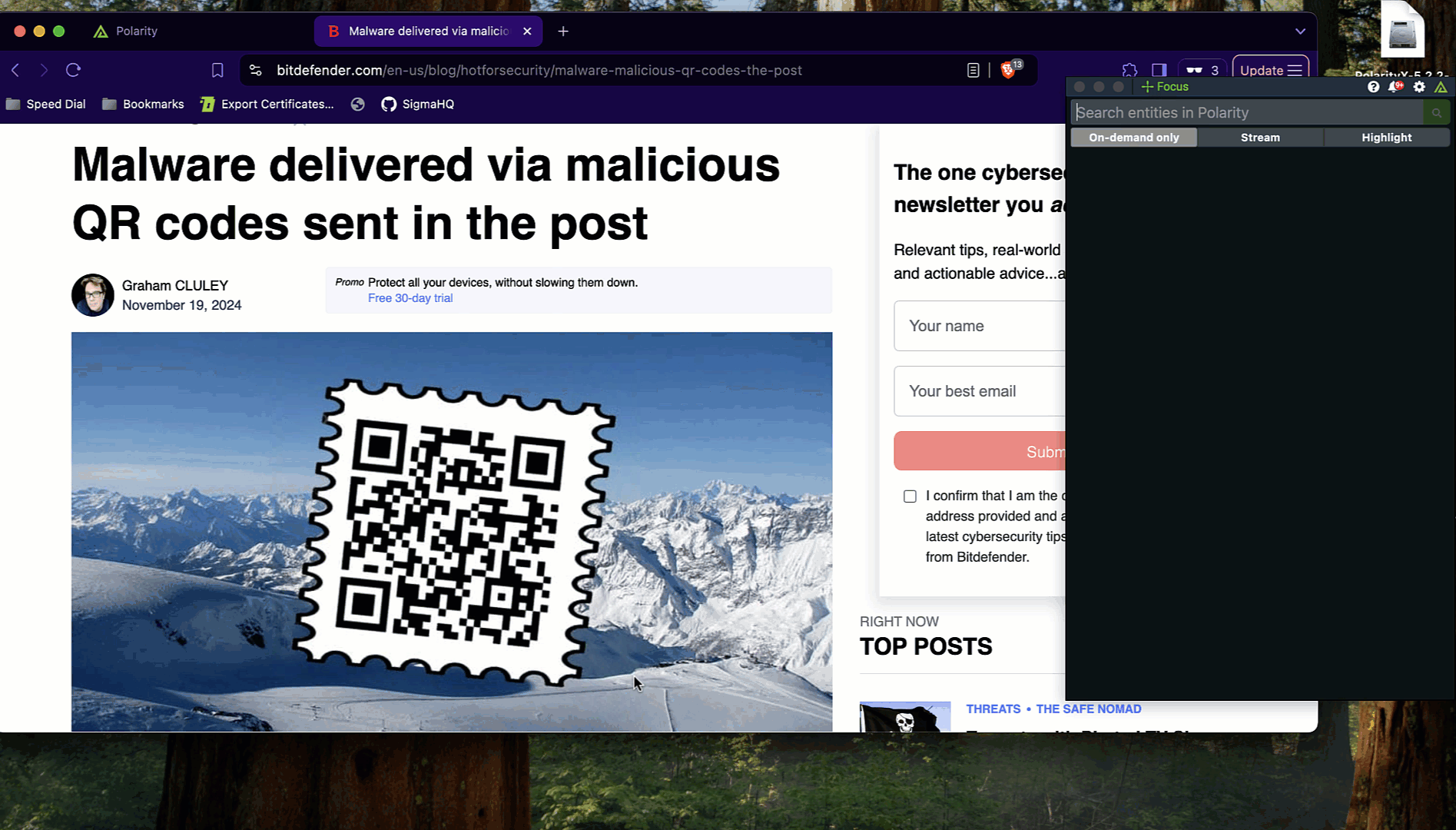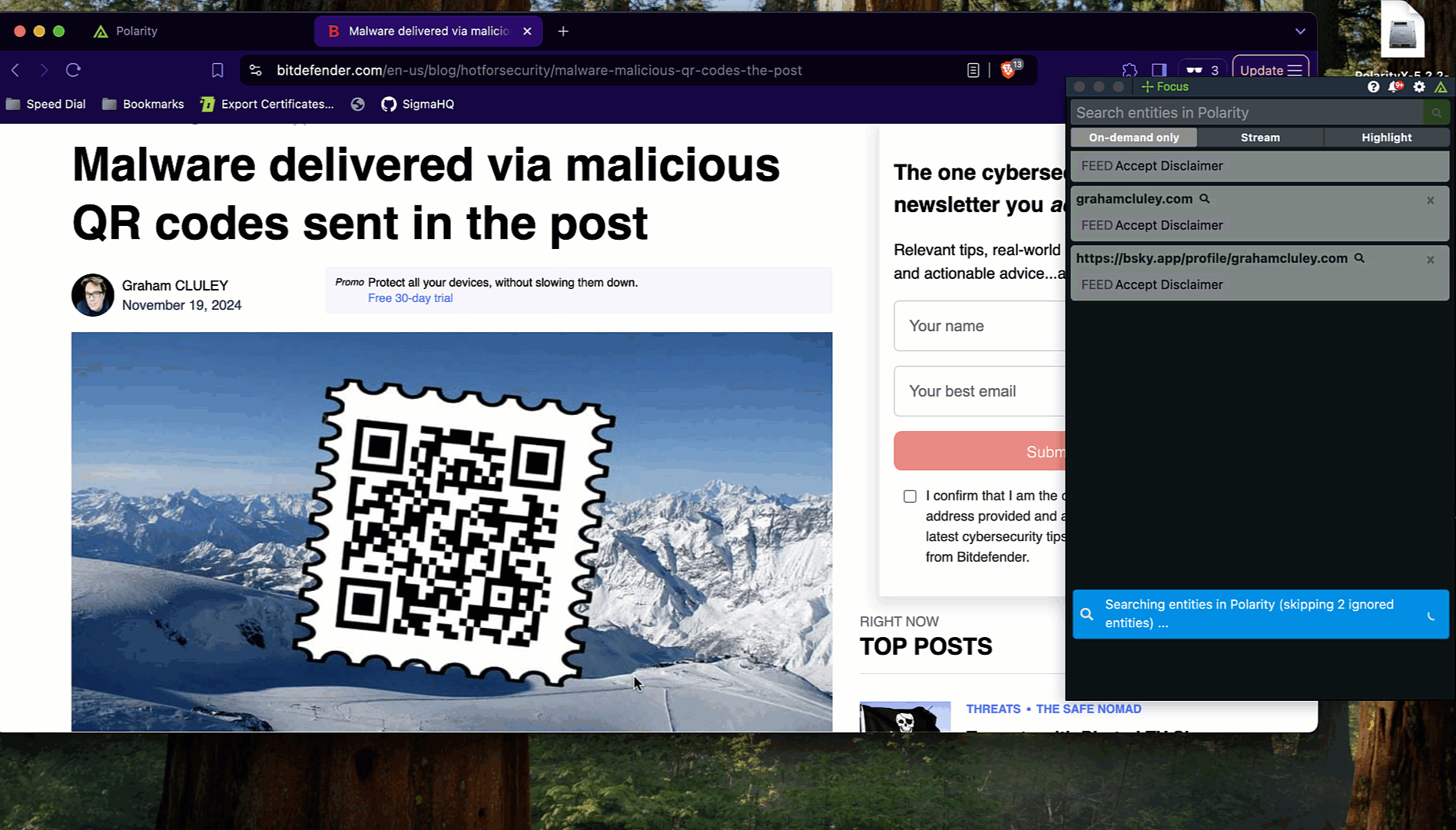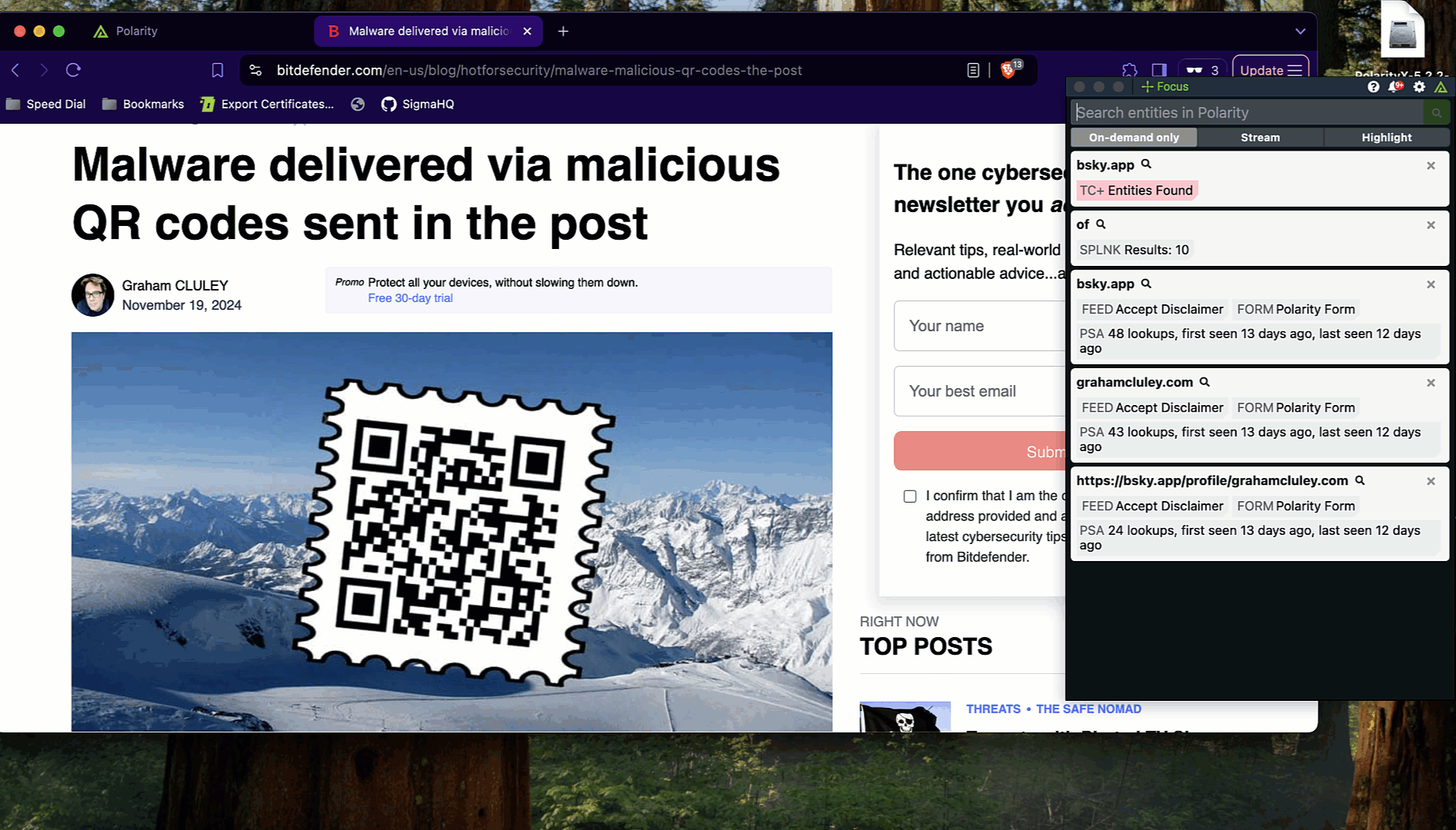
With this feature, Polarity enables analysts to extract and analyze the information embedded in QR codes, such as URLs, contact details, or other data. Polarity overlays actionable intelligence directly within the workflow, helping analysts:
- Recognize malicious indicators within seconds.
- Reduce the time spent deciphering QR codes.
- Make informed decisions faster.
How It Works:
1. Analysts trigger Polarity’s Focus Mode using the button or shortcut keys.
2. They use the reticule to highlight the QR code.
3. Polarity extracts the embedded information and cross-references it against its intelligence framework.
Within moments, analysts receive actionable insights on whether the QR code contains malicious indicators, allowing them to respond swiftly and accurately.
Defend Against Phishing with Confidence
The combined power of ThreatConnect and Polarity delivers an advanced, intelligence-driven approach to phishing threats, from email-borne attacks to QR code exploits. By equipping security teams with cutting-edge tools, real-time insights, and seamless integrations, these solutions empower organizations to defend proactively and efficiently.
Request a Demo Today to see how ThreatConnect and Polarity can strengthen your defenses against phishing threats.

