Posted
Today’s post continues an ongoing series on Polarity Use Cases. With a solution that overlays on any screen you’re looking at, Polarity has as many use cases as you do tasks in your workflow. Using Polarity, you’ll be armed with data awareness and recall so you can make better decisions, faster. This example showcases our DLP Use Case.
What is Data Loss Prevention?
Some of the biggest threats to your organization may be coming from the inside, in the form of unintentional or intentionally non-malicious incidents, or intentionally malicious data breaches. Data Loss is one of the main ways this can happen. For example, an employee might unknowingly send sensitive information outside of your organization’s network to a prospect, vendor, or to a larger mailing list.
This is where Data Loss Prevention (DLP) processes play a critical role: it’s “a strategy for making sure that end users do not send sensitive or critical information outside the corporate network. The term is also used to describe software products that help a network administrator control what data end users can transfer.” Traditionally, those products fall into three categories: Network, Endpoint, and Sensitive Information Leakage.
How does Polarity help DLP?
Polarity does two things: it allows you to see your data even clearer by providing contextual information on the fly, but it also allows you to take those insights into every other DLP tool you use, whether it’s a Network, Endpoint, or Sensitive Information Leakage solution (if you need a refresher on these core DLP solutions, we included one below). It does this with augmented reality, but in software, on your desktop. It uses computer vision to recognize what is on an analyst’s screen and then overlays relevant contextual information in real-time.
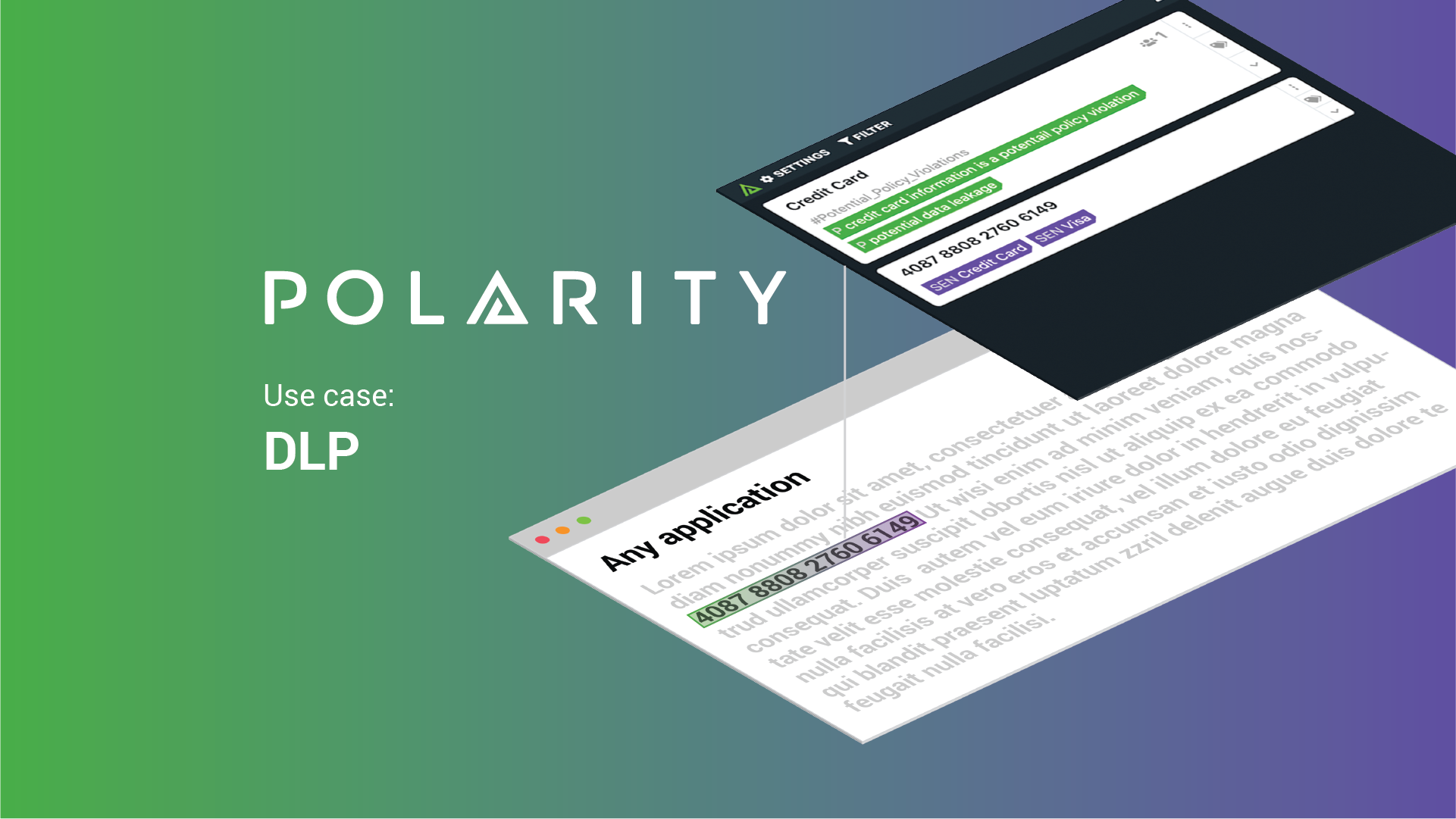
Data Awareness
This unique functionality enables teams to instantly spot and flag sensitive information like social security numbers, credit card numbers, email addresses, and more.
Integrating with your Existing DLP Tools
Additionally, Polarity has the ability to augment your existing DLP tools. Polarity will give you complete visibility into your Network DLP tool anytime you are looking at network logs, giving you immediate contextual information and removing the need for any querying, switching between windows, and performing lookups. Polarity will also augment your Endpoint DLP solution by giving you instant data awareness on any information that might be trying to leave your network, or has already left your network.
Identify Incidents Faster
With Polarity, you can identify if there has been an incident much faster by having all of the information you need immediately, no searching necessary. Our augmented reality for your desktop helps you make better decisions, faster.
What are DLP best practices?
If you need a refresher on DLP best practices and solutions, we’ve compiled some information on different tools and best practices here. DLP can be implemented by defining what information is sensitive to your organization, putting in place preventative security policies, and using DLP tools.
Defining Sensitive Information
Unless everyone at your company is aware of what information is considered sensitive, you will have a big problem with data loss that originates from small differences in individual judgment. Have a clear cut guide available to employees to show them what is ok to share outside the organization and what is not. This education should ideally occur during new employee onboarding to set a secure standard from the beginning.
Policy Implementation
The Business and IT departments of your organization should collaborate on setting policies for DLP. In the early stages, identify:
- Data categories that have been singled out
- Steps that need to be implemented to combat malpractice
- Future growth of the DLP strategy
- Steps that need to be taken if there is an abnormal occurrence.
After you’ve set policies, implementation should be an ongoing practice of establishing rules, educating employees, and re-evaluating policies.
DLP Tools
This brings us back to our three main types of DLP: Network, Endpoint, and Sensitive Information Leakage. DLP tools fall into these buckets, each providing different benefits. Some organizations go with one, some opt for all three. Your choice in tool will depend on the specific needs of your company.
In general, these tools come “pre-built with policies suitable for compliance with standards such as GDPR, HIPAA, or PCI-DSS. Once DLP software identifies a breach in policy, protective measures are taken, such as alerts and data encryption. DLP software also monitors endpoint movement, and safeguards data at rest, in motion and in use.”
Types of DLPSolutions
There are three main types of DLP: Network, Endpoint, and Sensitive Information Leakage.
Network DLP
Network DLP monitors all traffic through ports on a network, allowing organizations to to encrypt data, block risky information from leaving the system, and ultimately control the sharing of sensitive data on your network to enforce the DLP policies you’ve implemented. These solutions enable teams to monitor and control email and web application traffic, flag sensitive content, encrypt email content, and more.
Endpoint DLP
Endpoint DLP deploys agents installed on workstations and devices that will prevent the transfer of information. Organizations can automate the blocking of sensitive information, and continuously log actions, enabling them to prevent data loss before it happens.
Sensitive Information Leakage
Sensitive Information Leakage monitors the use of sensitive information internally and externally to an organization. Sensitive information can be customized to indicate certain types of content over others, and confidence and proximity can also be used in the evaluation.