Posted
Today’s post continues an ongoing series on Polarity Use Cases. Data tells a story, Polarity helps you see it with Augmented Reality overlaying contextual information as you work, giving you the right data at the right time to make informed decisions and take action with speed. No glasses or goggles required, Polarity is software that works in a wide range of use cases. This example showcases how an analyst might use Polarity with CVEs.
View this post with Polarity for an added bonus!
- If you already have Polarity, just add the latest version of the “Polarity Blog Challenge” Reference Channel to your instance. You can download this Reference Channel from the GitHub repo.
- If you don’t have Polarity, sign-up for the trial, then just add the latest version of the “Polarity Blog Challenge” Reference Channel to your instance. You can download this Reference Channel from the GitHub repo.
With the special Reference Channel enabled, you’ll see the power of Polarity’s software-based Augmented Reality right in this blog post!
Analyzing CVEs with the Right Data at the Right Time
Despite hundreds of security products being available in the market and dozens deployed by most security teams, the time needed to detect and investigate events as well as respond to attacks continues to increase. This problem results from a number of factors, yet surprisingly one of the greatest causes is data.
While the answer to nearly any question faced in security teams relies on data, having the right data at the right time is a challenge that can affect teams trying to make informed decisions and act with speed.
Security teams especially struggle with spending a large amount of their valuable time querying intelligence (e.g. URLs, hashes), reviewing SIEM events, searching tickets for information, and looking-up assets and owners; in other words, working with data. The teams have data from these sources and others, but need to perform repetitive queries against multiple data sources in order to see the full story in it. In fact, the approach most teams use to analyze something as routine as a CVE entry illustrates the point; it is tedious work that spans a number of tools and data sources.
It was security analysis challenges like investigating CVEs or any other security events that led our founders to build Polarity – a unique platform that uses software-based Augmented Reality to overlay contextual information needed to make decisions, exactly when you need it. Polarity brings together what you know, your teammates know, and what’s known by all the tools you use in your security team, so you can see the full story in the data. Armed with the right data at the right time, what we call Data Awareness and Recall, results in informed decisions and fast action.
With Polarity, teams can reclaim the time they spend querying and switching between products, greatly improve team-wide knowledge sharing, and avoid missing important information that is needed to do their jobs.
Analyzing CVEs with Polarity
Investigating CVEs is a common task for Vulnerability Management teams, Pen Testers, and Red Teamers. Analysts use a wide range of tools to complete the job with some teams investigating dozens or more CVEs per day. The process likely includes assessing important details such as IPs, security databases, and tickets, and taking steps to remediate if a vulnerability is detected. From start to finish, it could take hours for each investigation while the analyst references various tools, messages, and tickets.
Here’s how Polarity could help different analysts understand CVEs:
Vulnerability Management Teams
Reading a New Threat Intel Report on the Latest CVEs
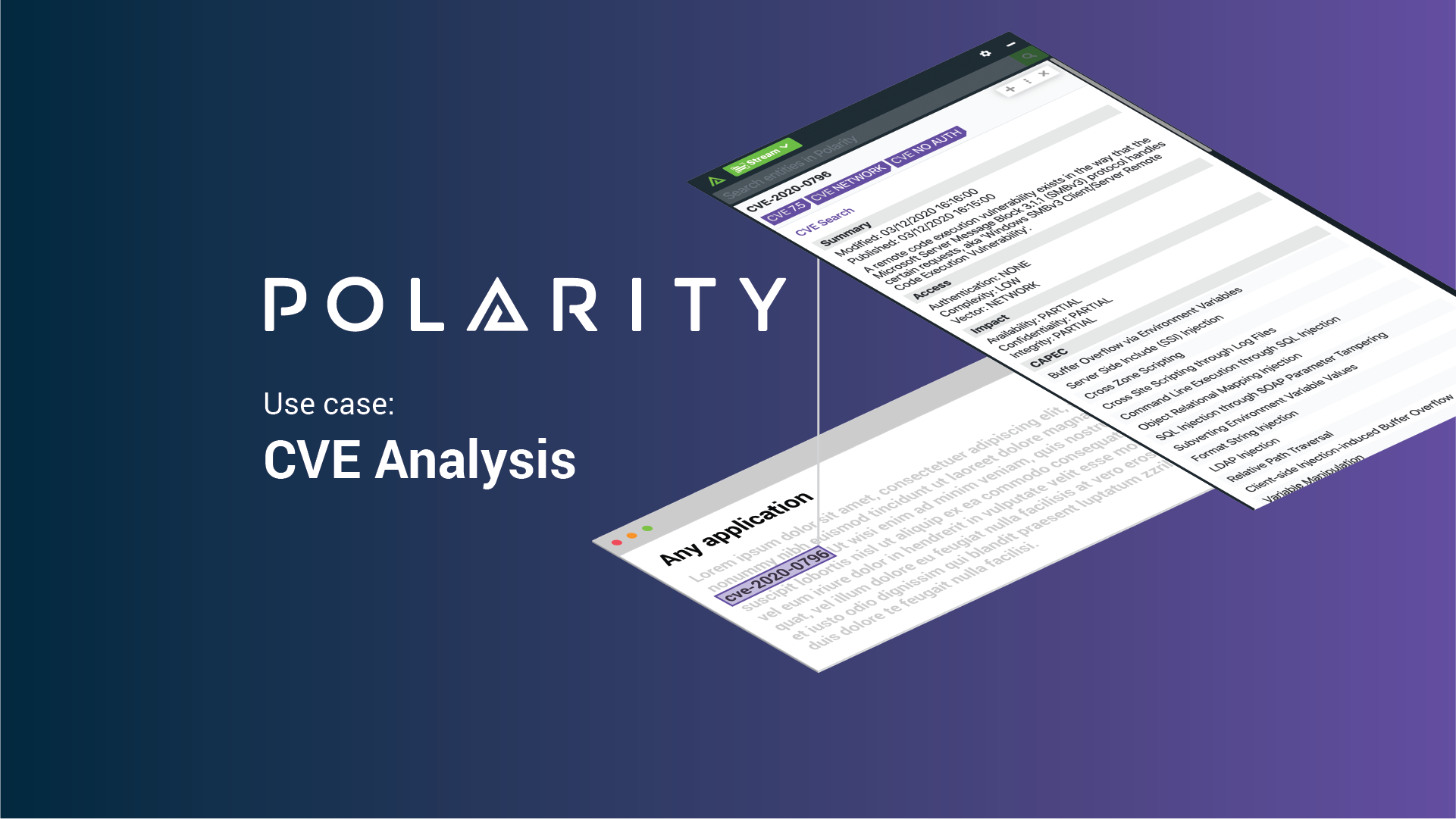
A Vulnerability Management analyst can gain complete data awareness on a CVE through the Polarity-Vuldb-VulnDB or CVE Search integrations. Polarity will simply recognize on-screen text and match it with contextual information from these integrations, giving the analyst a holistic understanding of the CVE. The analyst can also pivot out to Exploit DB or Twitter through Polarity’s Google Custom Search Engine integration. This level of data awareness and recall for all of the analyst’s tools enables them to have a faster and deeper understanding of the latest vulnerabilities affecting their internal assets.
Triaging a Vulnerability Scanner Report
Polarity will recognize and highlight text in a Vulnerability Scanner Report, providing contextual information to immediately alert the analyst to which assets are affected, enabling the analyst to triage them quicker.
Testers and Red Teamers
While a Pen Tester or Red Teamer analyzes CVEs, Polarity will scan the IP Range to associated software services, then look up associated CVEs to determine exploits. Once a particular CVE is identified, Polarity will research systems that are exploitable by that CVE and provide that contextual information to the analyst.
Armed with Polarity’s software-based Augmented Reality for data, the analyst was able to get the contextual information needed to make decisions about the CVE exactly when it was needed. Polarity brings together what’s known by all the tools they use in the security team, what the analyst knew, and what his teammates knew, so the analyst could see the full story in the data. Armed with the right data at the right time, what Polarity calls data awareness and recall, resulted in an informed decision and fast action.
With Polarity’s 100+ powerful, open-source integrations, you can get immediate access to the data in your tools without pivoting into those tools and searching them for information. Integrations also allow you to direct other tools to take action, for example updating a ticket in your ticketing system. Vuln Management, Pen Testing, and Red Teams especially benefit from our integrations with platforms like VulnDB, CVE Search, Nexpose, Tenable, Google Custom Search Engine, and many others.
See Polarity in Action
Want to learn more? For a deeper understanding, watch our CEO demo Polarity.