Posted
Maximizing your Splunk Investment with Polarity
In the ever-evolving landscape of cybersecurity threats, organizations need to be prepared to investigate and respond to incidents immediately, and with confidence. Splunk plays a crucial role in this process for many organizations. Many teams need to respond to more attacks than ever before, often with less time and resources to do it. The average time it takes to detect and remediate a breach is 287 days, and growing.
With Polarity, users can automatically search across all of their data sources for Indicators of Compromise (IOC), including in their Splunk deployments. By utilizing Polarity’s Splunk integrations, a CISO can have the confidence that their team is running the right queries every time, no matter how Senior or Junior they are. With the right set of queries to run automatically, analysts can efficiently navigate through vast amounts of data to identify and mitigate potential security incidents. In this blog, we will explore five powerful Splunk queries that Senior Cyber Security Analysts would normally run manually, but that can be automated with Polarity to kickstart an investigation.
When searching Splunk environments, Polarity uses the {{ENTITY}} field to automatically add the IOC the analyst is looking for to the Splunk query. This enables even Junior analysts to quickly, and confidently search through their data without having to know how to write a Splunk query.
1. Our first query helps when investigating network traffic, to see if an IP Address has been seen in Splunk.
tag=network tag=communicate (src_ip=”{{ENTITY}}” OR dest_ip=”{{ENTITY}}” | head 10
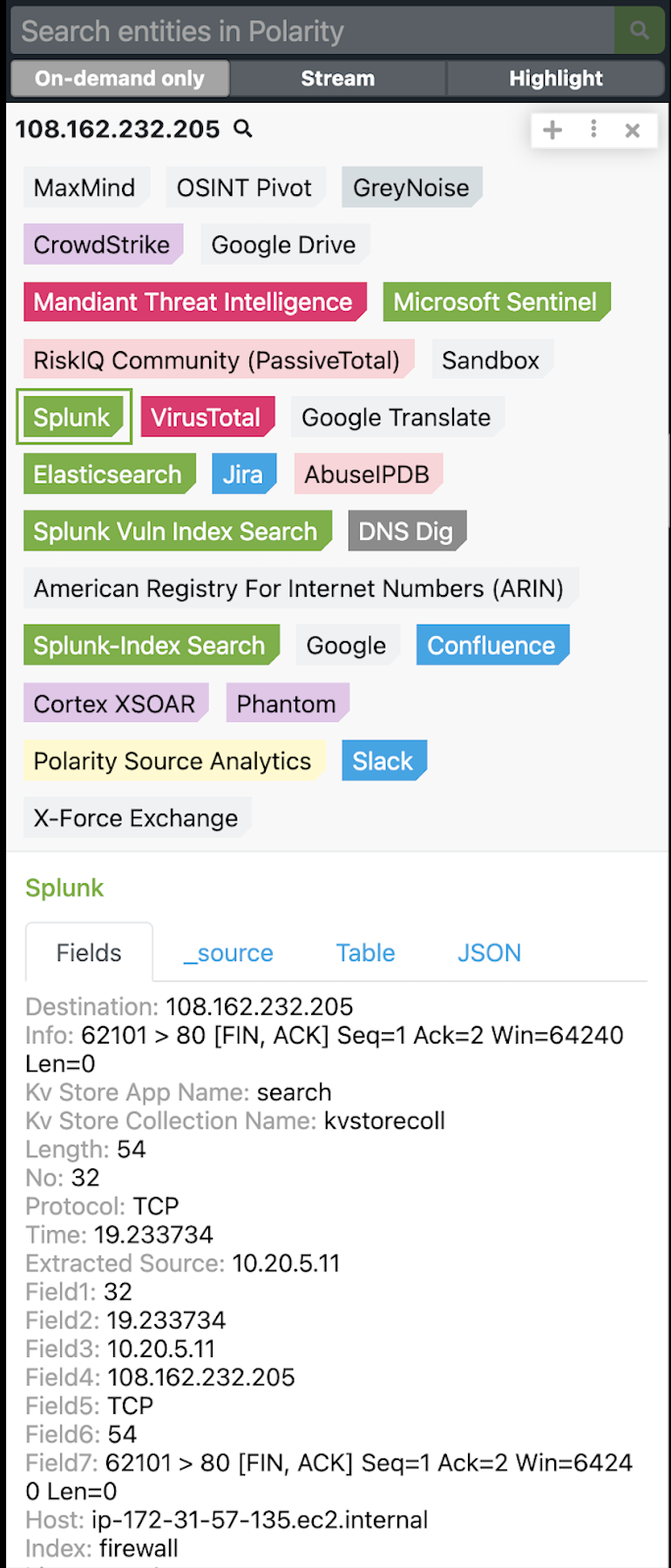
By searching with Polarity, the analyst will automatically search across all of their connected data sources, including Threat Intelligence Providers, to see if the IP address is malicious as well as insights into if and where it has been seen in their Splunk deployment.
2. Our second query helps when auditing Windows endpoints to find failed login attempts, which is required by many compliance audits like PCI, RMF, CMMC and many others.
source=”*wineventlog:security” ((EventCode=4625 AND ta_windows_action!=error) OR EventCode=529 OR EventCode=530 OR EventCode=531 OR EventCode=532 OR EventCode=533 OR EventCode=534 OR EventCode=535 OR EventCode=536 OR EventCode=537 OR EventCode=539) dest=”{{ENTITY}}”
Here is another query that can work for detecting failed login attempts, this time by user:
tag=“authentication” action=“failure” (user={{ENTITY}} OR src_user={{ENTITY}})
3. One common technique our adversaries use when compromising an endpoint is to create processes, or hide behind known binaries to escalate privileges and run commands. Our third query is similar to our second, and helps analysts quickly determine if processes have been created on Windows endpoints, and what those processes were.
source=“wineventlog:security” dest={{ENTITY}} EventCode=4688
4. When investigating phishing attacks or malware, analysts are often using a file hash as a starting point to determine if a file is malicious, and if it exists on any endpoints in their environment. Polarity allows users to search across all of their data sources, both internal and external, in parallel to determine if the file is malicious, and search Splunk to see if it exists.
This is where our fourth query comes in very handy.
source=“wineventlog:microsoft-windows-sysmon/operational” (MD5={{ENTITY}} OR SHA1={{ENTITY}} OR IMPHASH={{ENTITY}} OR SHA256={{ENTITY}})
5. For our friends that use Linux, there are also Splunk queries that can help you out. Our fifth and final search is used to look for privilege escalation attempts with Splunk.
sourcetype=linux_secure host={{ENTITY}} su* | where user!=root AND user!=””
Being equipped with the right Splunk queries automatically with Polarity significantly expedites the investigation process for Senior and Junior Analysts alike. The queries mentioned in this blog act as a starting point, allowing analysts to delve deeper into various facets of security incidents with confidence.
Remember, the key to successful investigations lies in leveraging the power of Polarity to enhance analyst’s ability to use Splunk’s extensive search capabilities without having previous knowledge of the Splunk Query Language.

There are many other Splunk queries that can be used with Polarity to enhance an organization’s ability to respond with speed and confidence. Watch our webinar to learn more: Maximize your Splunk Investment with Polarity’s Splunk Integration

