Automated Malware Analysis
Leverage malware analysis tools to classify, identify and capture malware indicators and context in a unified threat library to improve time to detect and respond.
Leverage Leading Malware Analysis Tools
Using malware analysis tools is vital for identifying indicators and gaining context on threats. Automate file sample submissions for analysis and report output ingestion and processing.
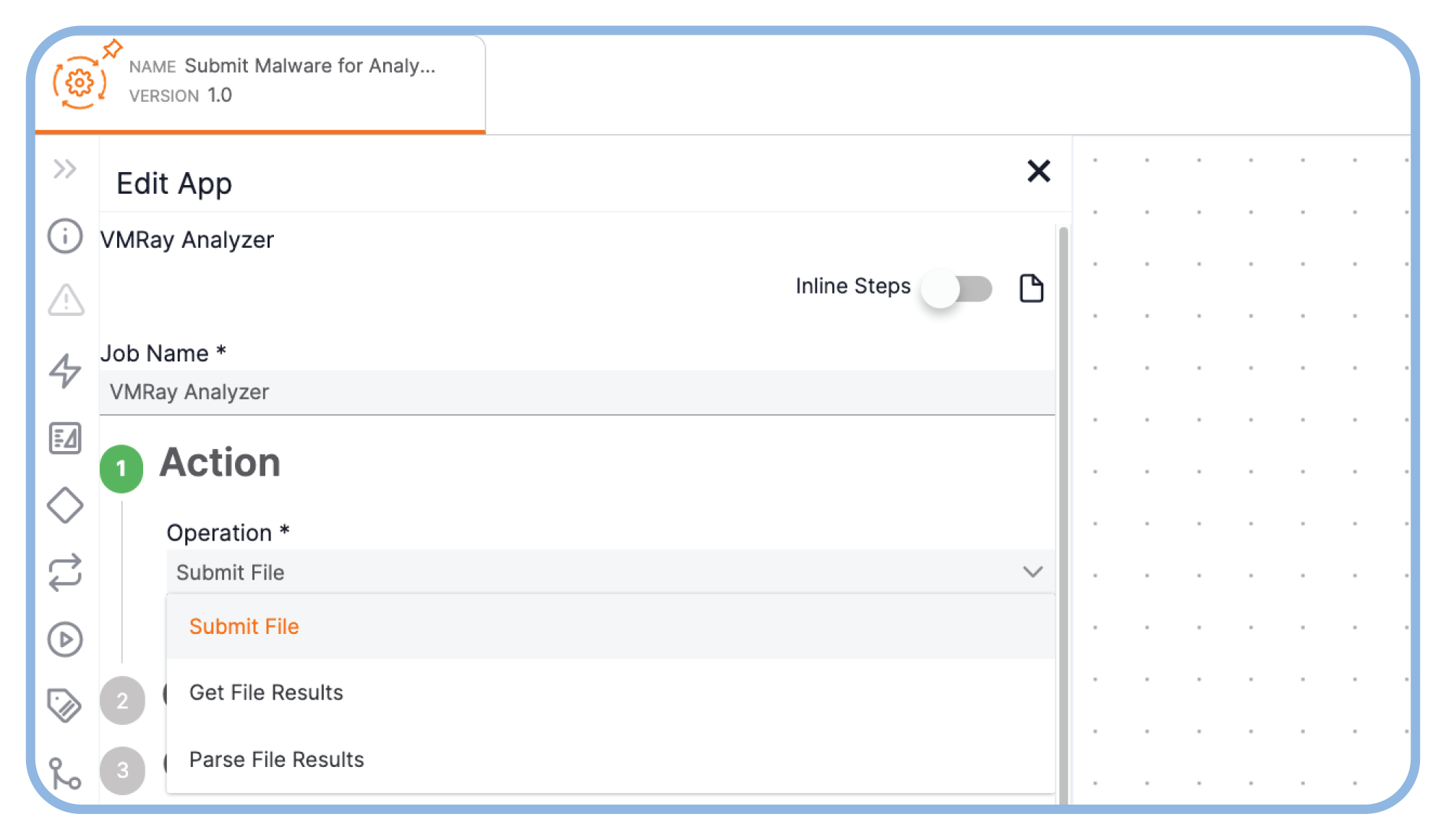
Respond Faster to Attacks
Use intel from malware analyses to speed analysis, threat detection and blocking, and incident response activities.
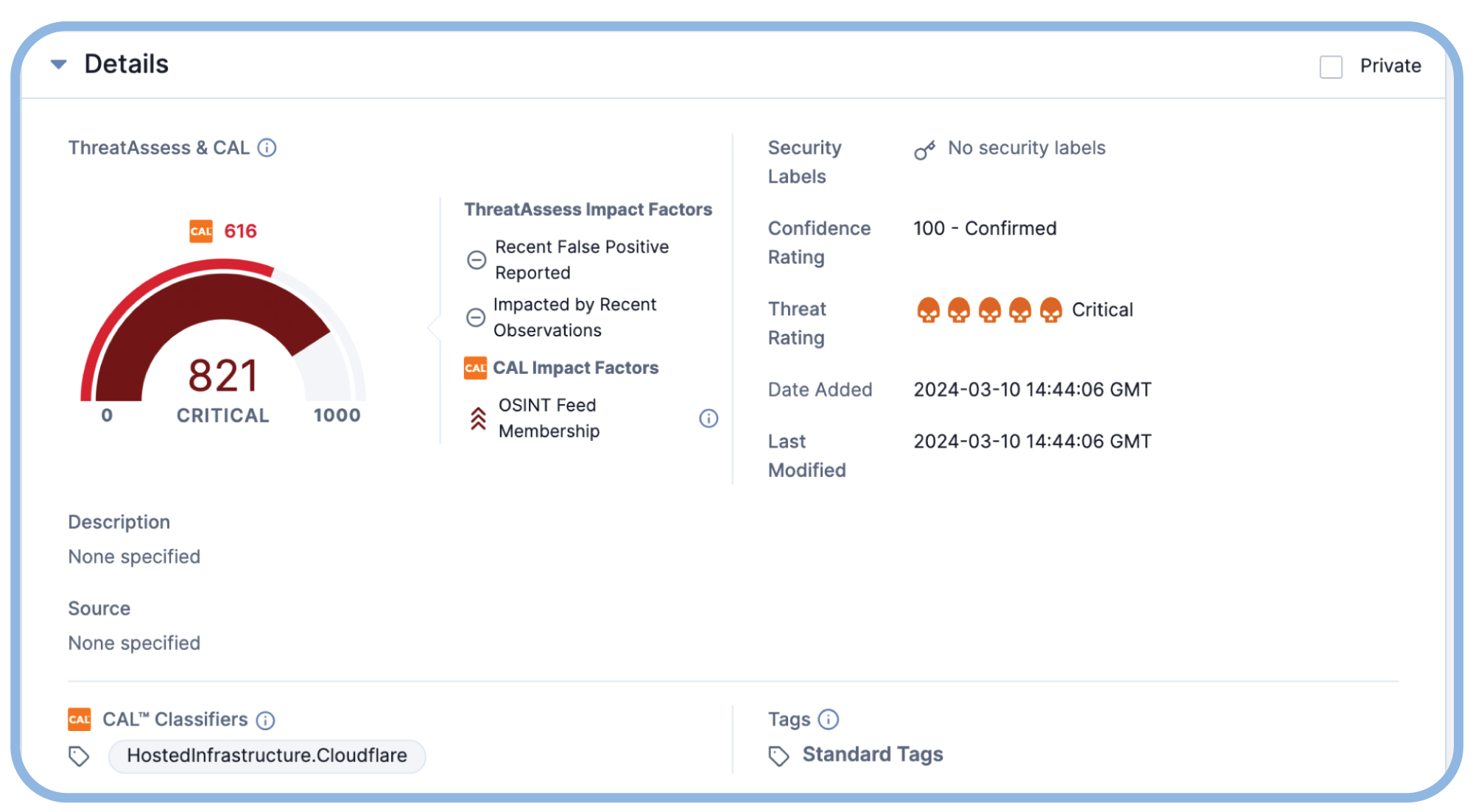
Automate Malware Search and Discovery
Leverage playbook automation and intel from malware analyses to determine the scope of an attack and speed response activities.
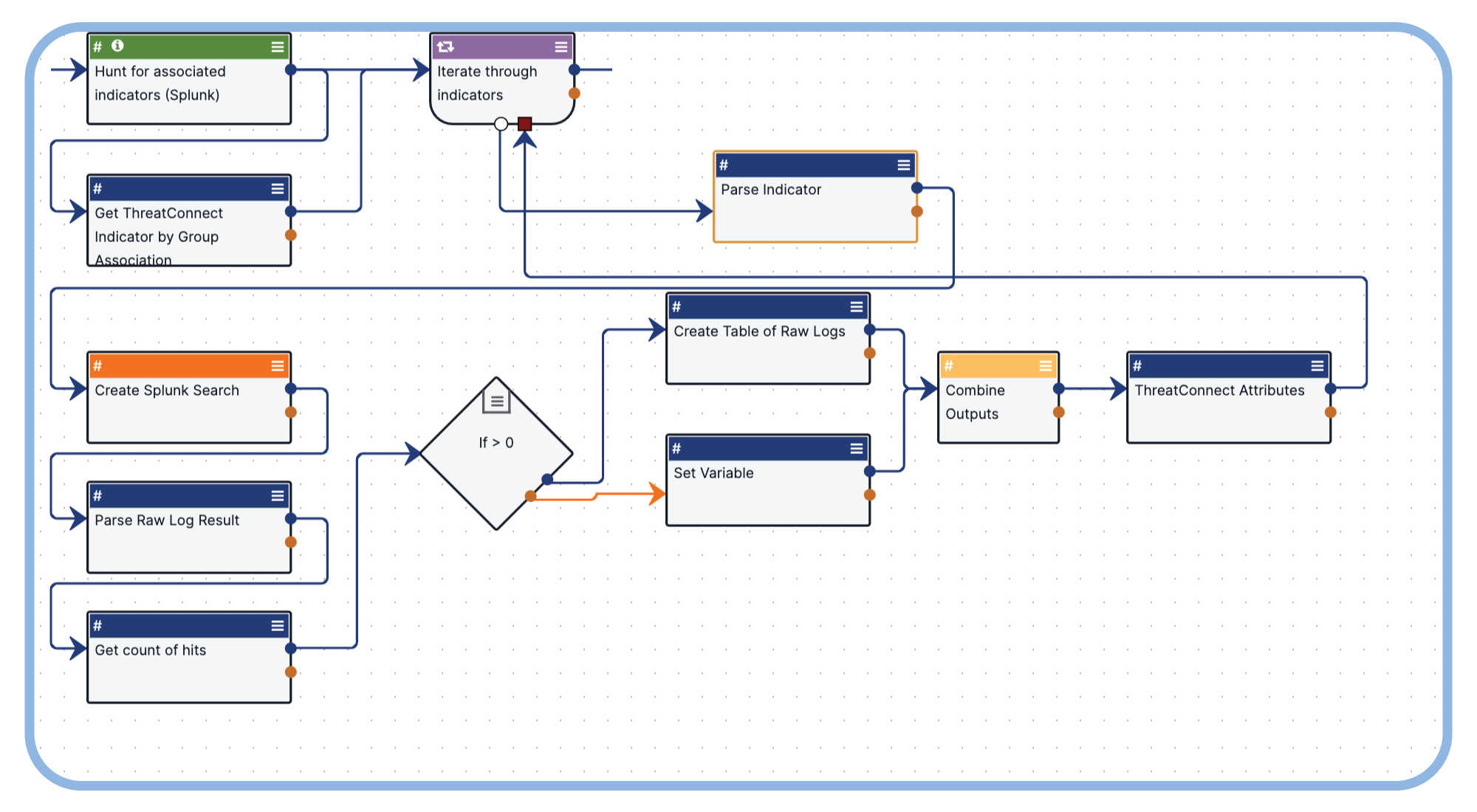
React Faster to Malware Attacks
Ask the Right Questions When Evaluating Threat Intel Platforms
Do you know the critical questions to ask when considering threat intel platforms?
Identify The Right Platform For Your Cyber Threat Intel Needs
Learn how to choose the right threat intel platform.
Operationalize Your Threat Intelligence
See the ThreatConnect TI Operations Platform in action
