Posted
The cybersecurity landscape is complex and fraught with many threats and vulnerabilities. Understanding and navigating this space requires access to up-to-date information on the activities of threat actors, which you can get through ThreatConnect ATT&CK Visualizer.
What is ATT&CK Visualizer?
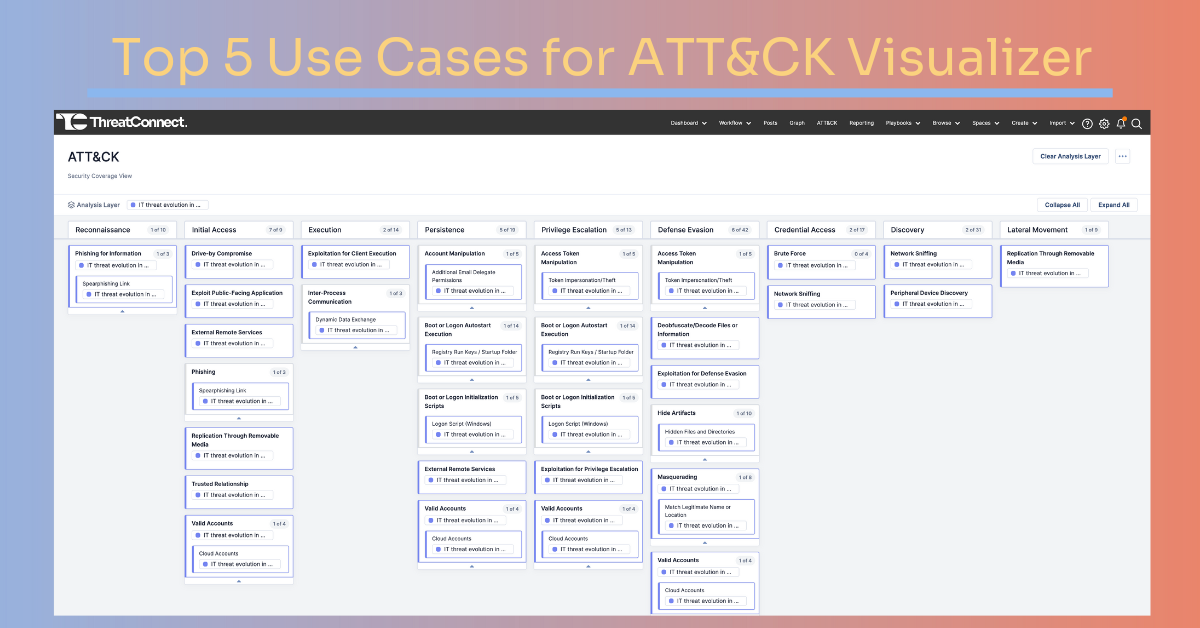
ThreatConnect ATT&CK Visualizer is our new interactive platform capability that visualizes the MITRE ATT&CK matrix of tactics, techniques, and sub-techniques. This matrix, developed by MITRE, is a globally accessible knowledge base of adversary tactics and techniques based on real-world observations. ATT&CK Visualizer automates the interpretation of ATT&CK data associated with threat intel and renders it in a user-friendly interface, similar to the ATT&CK Navigator.
Explore ATT&CK Visualizer with our interactive demo
Benefits of the ATT&CK Visualizer
ATT&CK Visualizer offers numerous benefits that make it an indispensable capability in the TI Ops platform.
Improved Threat Understanding: Visualizer makes it possible to understand complex attack techniques and tactics in a simple and accessible way. This facilitates more effective threat modeling and counter-strategy formulation.
Red Team/Blue Team Scenarios: ATT&CK Visualizer aids Red Teams in planning attacks using ATT&CK techniques and empowers Blue Teams to develop effective defense strategies.
Facilitates Incident Response Planning: By allowing users to see the sequence of an attack, Visualizer aids in planning reactive measures against an attack (i.e., malware, phishing, etc.). It helps prioritize response efforts based on understanding an attacker’s behavior and the techniques used.
Better Security Training: As an excellent educational tool, Visualizer helps illustrate complex attack techniques to less technical team members, fostering an understanding of how threat actors work.
Efficient Security Alignment: ATT&CK Visualizer helps to ensure the appropriate level of controls, budget, and staffing, avoiding excess and ensuring proper configuration.
The Top Use Cases for ATT&CK Visualizer
The ATT&CK Visualizer is a versatile tool with numerous applications. Here are some of its top use cases:
Threat Modeling – Threat modeling identifies potential threats to an organization’s assets and evaluates their potential impact. ATT&CK Visualizer has the ability to depict real-world attack scenarios in a familiar and easy-to-read format. Here’s how it’s beneficial for threat modeling:
- Visual Representation: Visualizer presents the MITRE ATT&CK matrix in a graphical format, making it easier to assist in your efforts to pinpoint how attackers might exploit vulnerabilities and move through different stages of an attack. This assists security analysts in understanding the attack chain and identifying potential weak points.
- Strategy Formulation: Armed with insights from Visualizer, security teams can formulate strategies to counter specific threats. They can prioritize which threat actors to address first and allocate resources more effectively to mitigate the most critical risks.
- Security Mapping: Security teams can use ATT&CK Visualizer to map their security controls coverage. This aids in identifying gaps in defenses and where there may be overspending and too much coverage. This helps with seeing where there are vulnerabilities and where to strengthen security measures.
Red Team/Blue Team Scenarios – ATT&CK Visualizer can be leveraged to support Red Teams and Blue Teams in real-world attack scenarios. Red teams plan attacks using ATT&CK techniques, while Blue teams develop effective defense strategies to counter those attacks.
- Red Team Simulation: The visualizer enables red teams to choose relevant techniques from the MITRE ATT&CK matrix, facilitating the creation of realistic attack scenarios. Red teams can visualize entire attack chains, identifying vulnerabilities and planning strategies to navigate through an organization’s defenses.
- Blue Team Defense Strategy: Blue teams can use Visualizer to comprehend potential attack scenarios in depth, aiding anticipation of attacker behavior and detection points. By studying techniques via ATT&CK Visualizer, blue teams can formulate proactive defense strategies and prioritize responses at different attack stages.
Incident Response Planning – Incident response is a crucial aspect of cybersecurity, and the ATT&CK Visualizer proves invaluable in planning reactive measures when a security breach occurs:
- Attack Sequence Visualization: Visualizer showcases the sequence of an attack, detailing the tactics and techniques used by adversaries. This visualization assists incident response teams in understanding how an attacker operates, e.g., business email compromise.
- Quick Decision-Making: Incident response teams can prioritize their efforts based on the attack’s progression. For instance, during or after an incident, security teams can map observed attacker behaviors to the ATT&CK Visualizer. This helps in understanding how a breach occurred, identifying gaps in defenses, and developing effective mitigation and remediation strategies. They can focus on halting the attack’s advancement, containing the breach, and remediating affected systems more effectively.
Security Training – Not everyone in an organization has a deep technical understanding of threats, which is where the ATT&CK Visualizer becomes a valuable educational tool:
- Simplifying Complexity: ATT&CK Visualizer breaks down complex attack techniques into easily digestible visual representations. This helps junior analysts, like Tier 1 SOC analysts, grasp the nature of cyber threats and their potential impact on the organization.
- Improve Knowledge: Security training sessions can use the ATT&CK Visualizer to provide a comprehensive overview of adversaries’ tactics and techniques. By mapping the ATT&CK techniques, they can identify which techniques they are capable of detecting and preventing and where there might be coverage gaps.
Efficient Security Alignment – ATT&CK Visualizer contributes significantly to aligning cybersecurity strategy with a more efficient approach:
- Risk Prioritization: ATT&CK Visualizer facilitates the organization and contextualization of the most up-to-date and relevant TTP data so security teams can focus on the most significant threats. This alignment ensures that security efforts are directed toward mitigating risks that align with the organization’s business goals.
- Resource Allocation: Because ATT&CK Visualizer reduces the amount of external research analysts would otherwise need to perform, organizations can allocate resources (people, budget) more efficiently. This prevents unnecessary expenditures on less relevant security measures.
ATT&CK Visualizer helps enhance understanding of threats, facilitates incident response, and drives effective security education. Whether you’re a seasoned security analyst or a novice, the ATT&CK Visualizer in the ThreatConnect Platform can significantly elevate your cybersecurity game.
Other Resources: