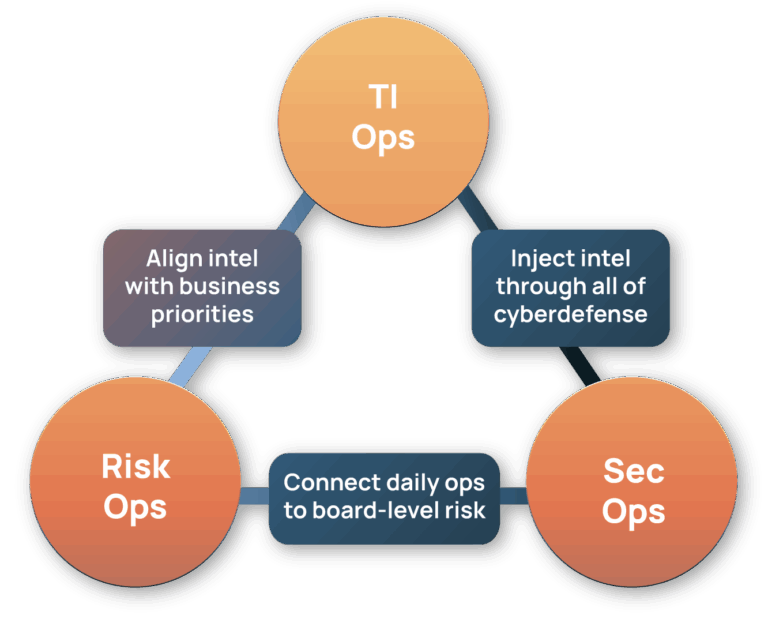
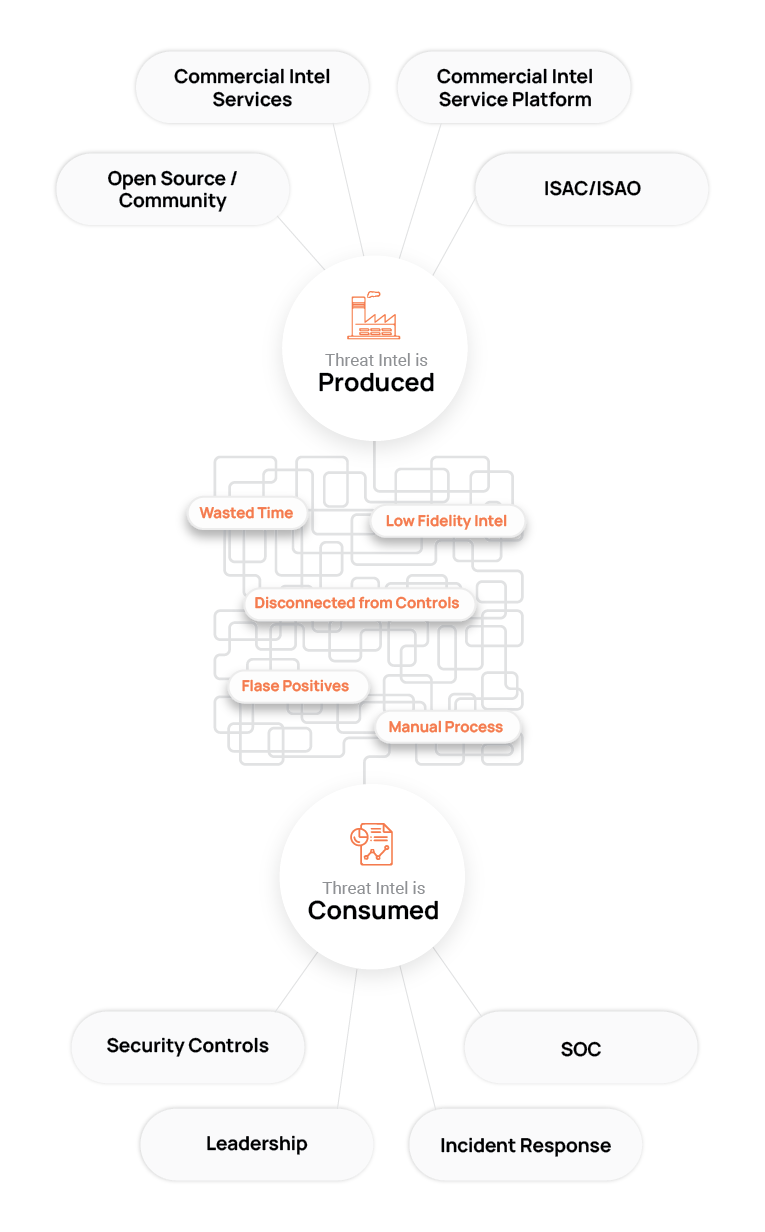
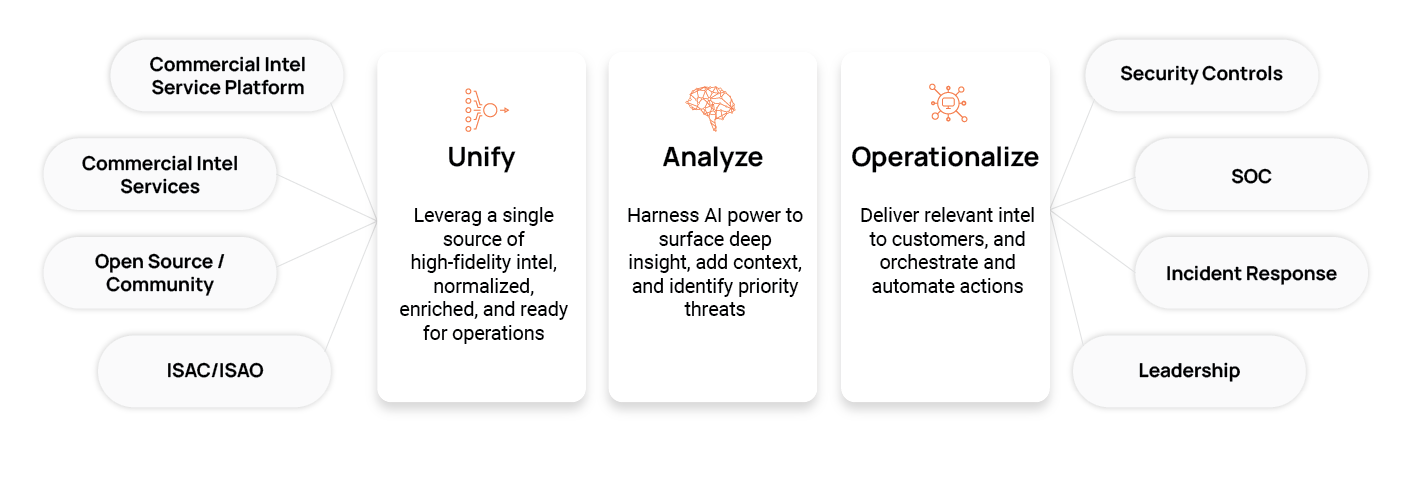
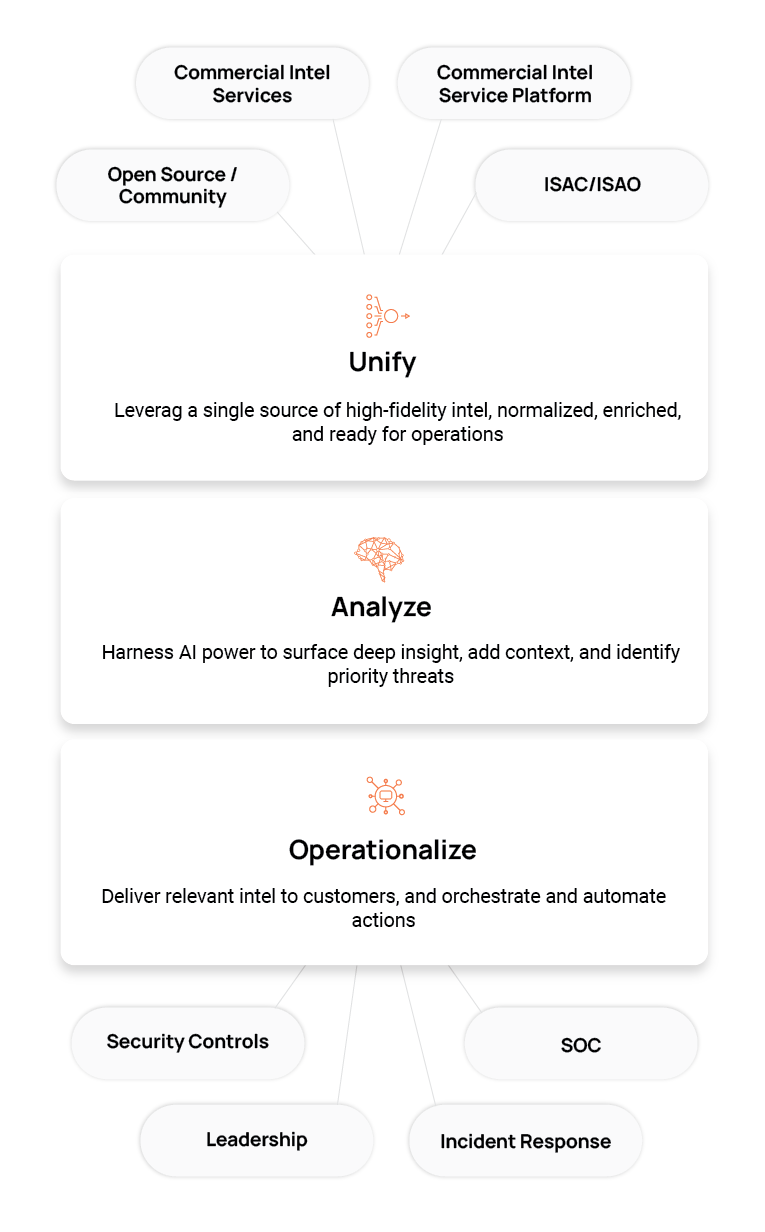
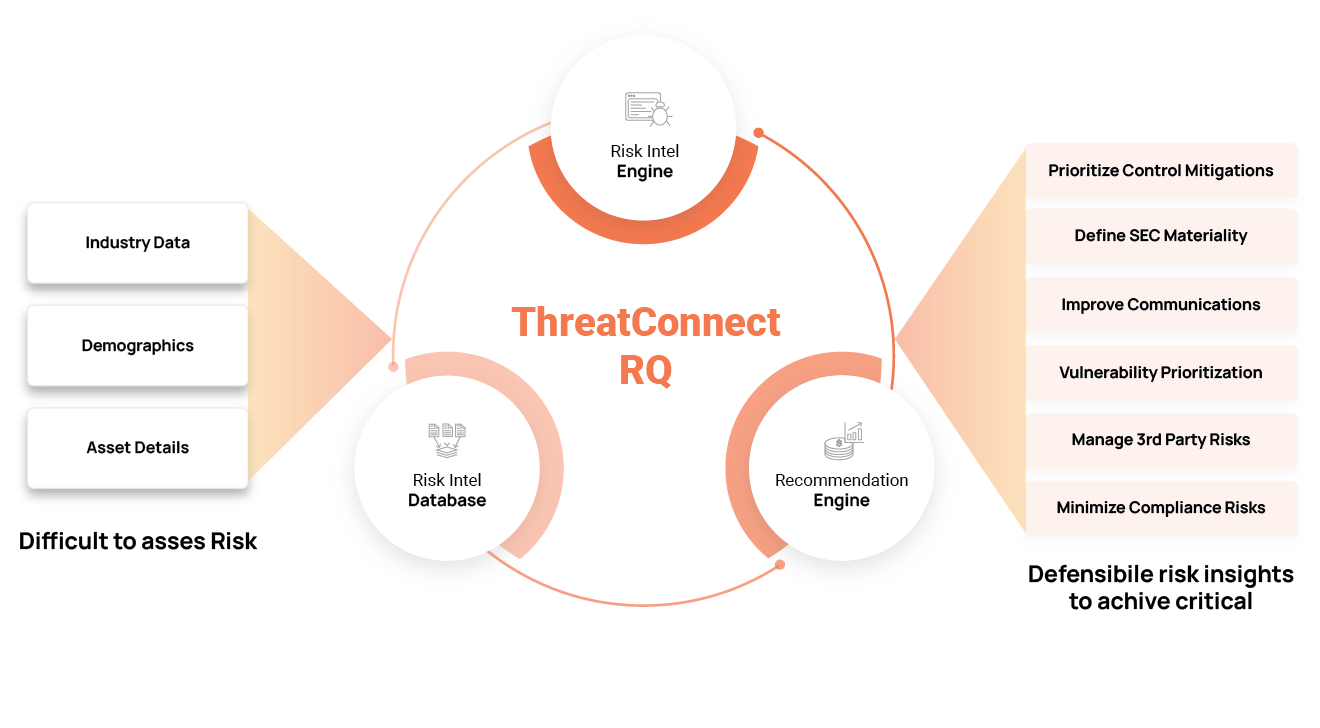
Buyer’s Guide for Threat Intelligence Operations
The ThreatConnect Buyer's Guide for Threat Intelligence Operations is a comprehensive resource tailored for cybersecurity leaders, strategists, architects, and analysts seeking to enhance their organization's security and risk posture by effectively utilizing cyber threat intelligence (CTI).