Threat and Risk Informed Cyber Defense Powered by AI
Operationalize Threat Intelligence
Put high-fidelity threat intelligence at the core security operations for more effective cyber defense
Unlock All Your Security Data
Federated search, correlation, and analysis puts intelligence and context at the point of decision
Quantify Cyber Risk
Prioritize security investments and defensive actions based on the greatest risks to your business
Make threat intelligence, security operations, and cyber risk management teams more effective, efficient, and collaborative with AI-powered solutions that enable the operationalization of high-fidelity threat and risk insights.
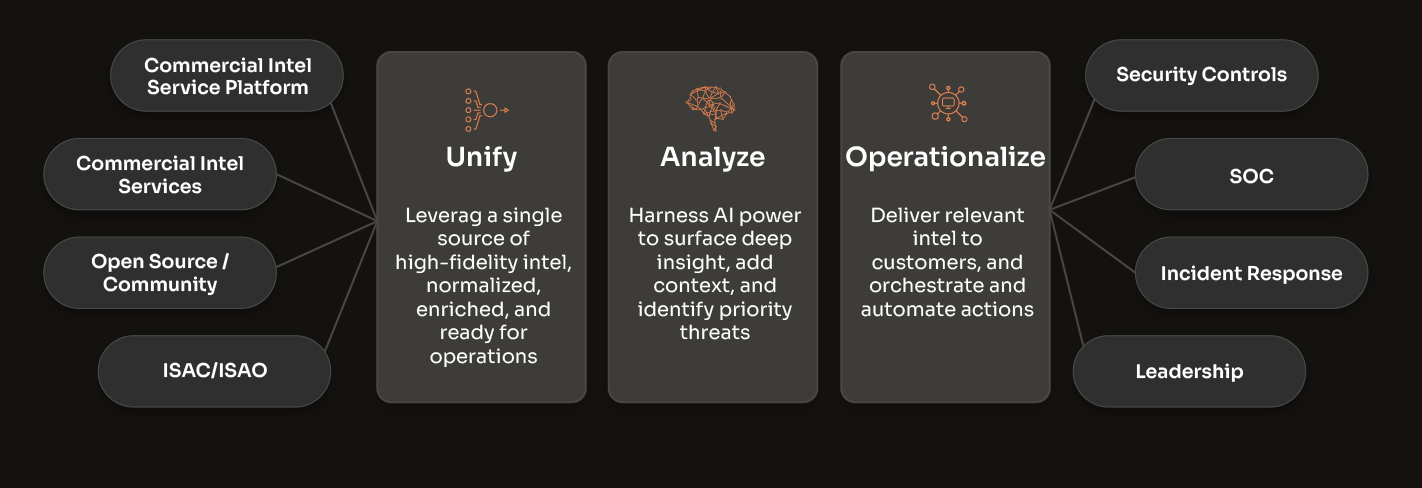
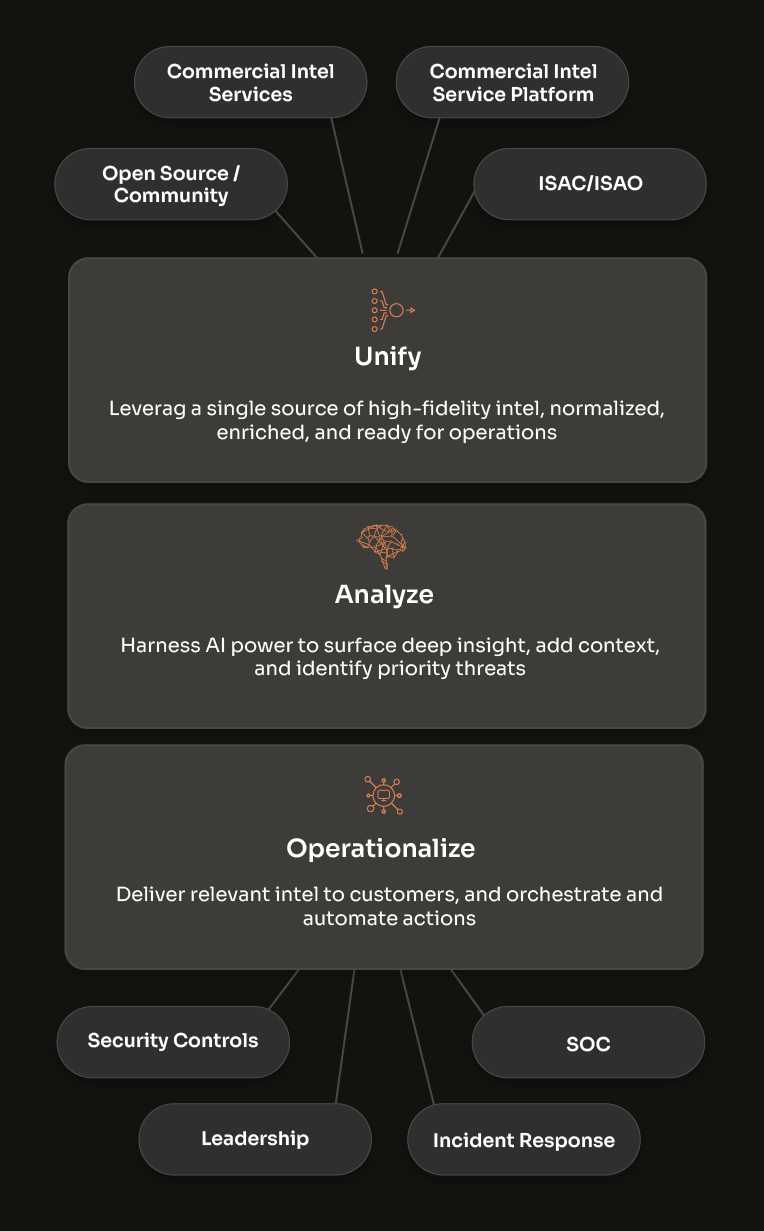
Threat Intelligence Operations
Evolve your cyber threat intelligence from simply intel managing to truly operationalizing it, ensuring a more informed and proactive cyber defense.
Benefits for Threat Intel
Producers
- Bring together all sources of open source, commercial, and internal intelligence
- Distill the intel volume into high-fidelity, actionable intelligence
- Shift the focus from intel collection and processing, to analysis and sharing
- Measure and demonstrate the value and impact of your CTI program
Benefits for Threat Intel
Consumers
- Relevant and actionable intel when, where, and how it’s needed
- Faster time to detect, prevent, and respond to threats
- Enhance cyber risk management
- Better collaboration and communications
Unnecessary Complexity Limits Intel Value
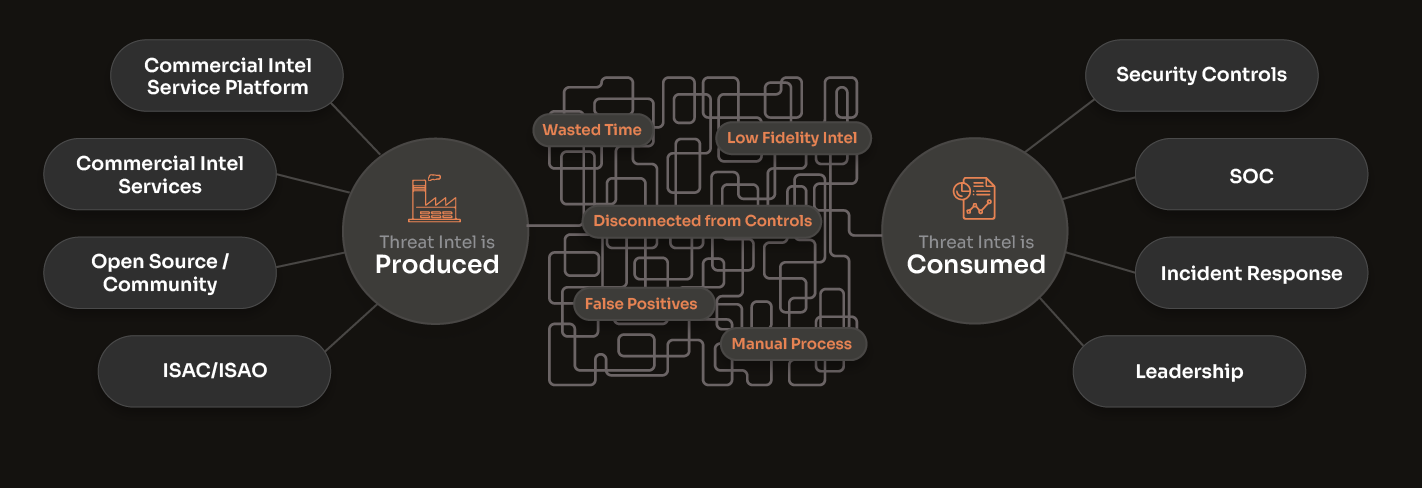
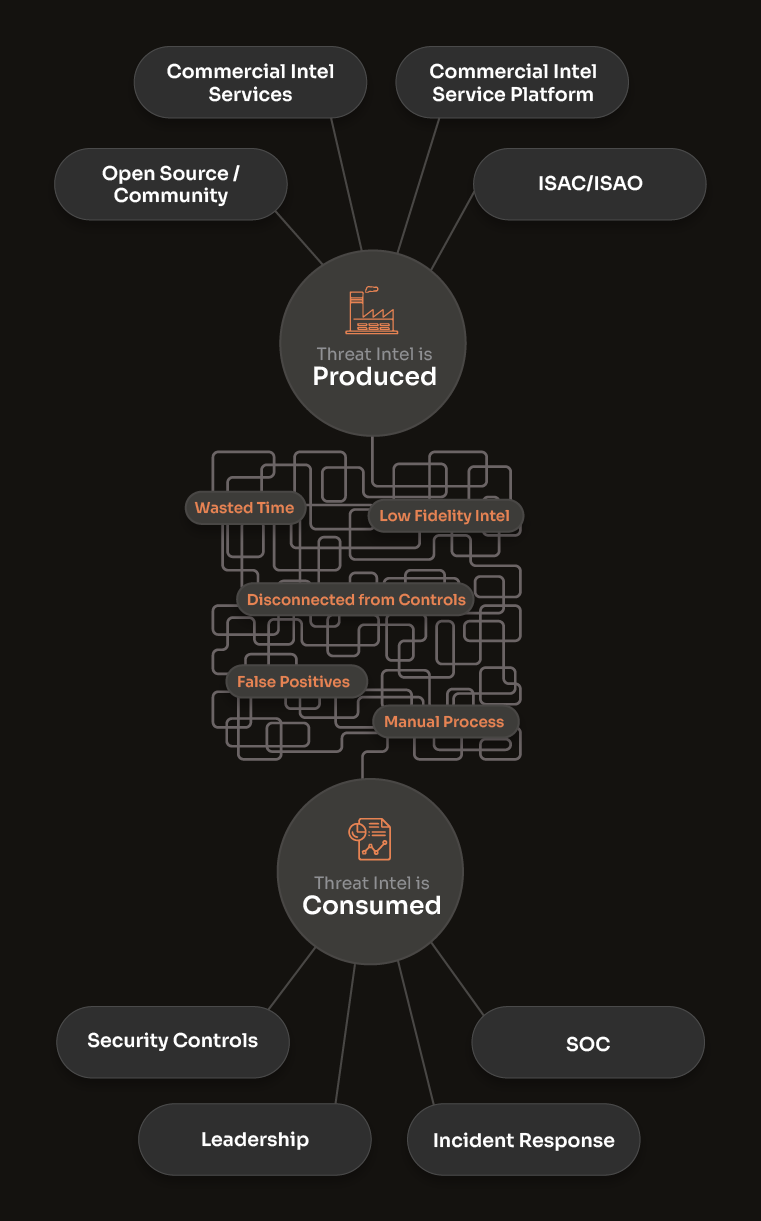
The Threat Intel Landscape is Complicated. Here's Your Guide.
Threat intel feeds and data services provide intelligence. Threat intelligence platforms let you manage and operationalize multiple sources of commercial, open-source, and internally generated intel.
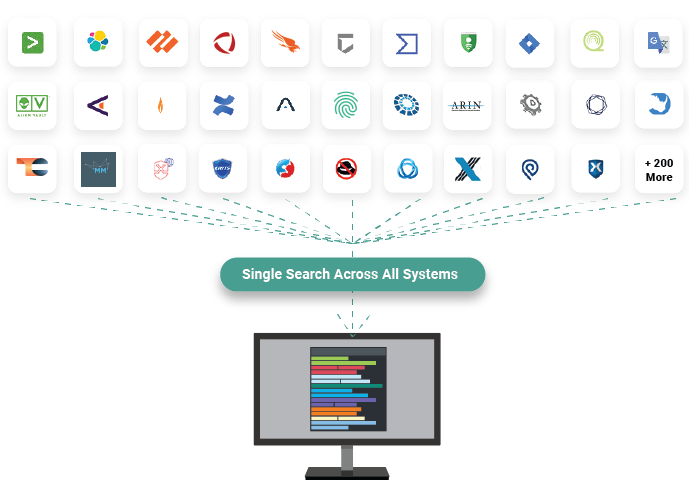
Unified threat intel, context, and knowledge at the point of analysis and decision-making
Polarity federated search, correlation, and analysis puts the data your analysts need at their fingertips at the time of decision.
- Analysts can access, analyze, and correlate all sources of intelligence, data, and knowledge in one place
- Cyber threat intelligence, security operations, incident response, and threat hunting teams have the information they need to make decisions
Without Polarity
With Polarity
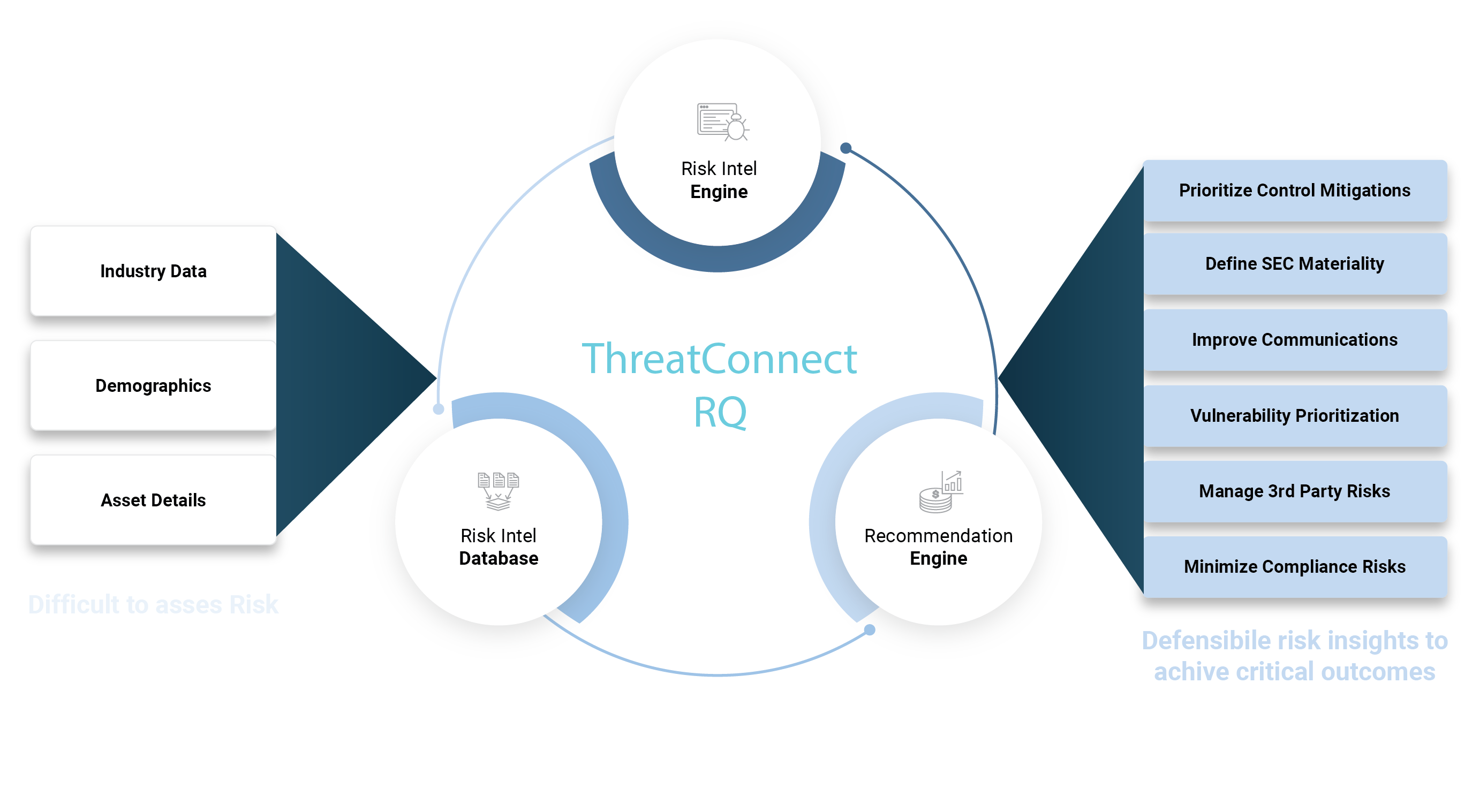
Cyber Risk Quantification
Quantify cyber risk in dollar terms to comply with regulations, evaluate controls, and improve board reporting.
- Get better decision-making knowing the financial impact from threats and security controls
- Prioritize and communicate ROI from cybersecurity investments
- Communicate cyber risk in business terms to executives and boards of directors
Trusted By Leading Companies
See how industry leaders are driving outcomes with the ThreatConnect platform.

Threat and Risk Intelligence Solutions
Buyer’s Guide for Threat Intelligence Platforms
Understand, evaluate, and select the right threat intelligence platform (TIP) for your organization.
Groundbreaking Federated Search
See how you can bring all your security data together for better decision-making and faster response.
Industry-leading Risk Quantification
Learn how ThreatConnect sets the industry standard for cyber risk quantification.