Posted
This Playbook allows you — without writing code — to automate the ingestion of Snort rules into the ThreatConnect Platform
A customer needed a short turnaround solution for bringing CrowdStrike’s Snort Ruleset and due to the relatively small dataset being worked with, Playbooks was the optimal solution.
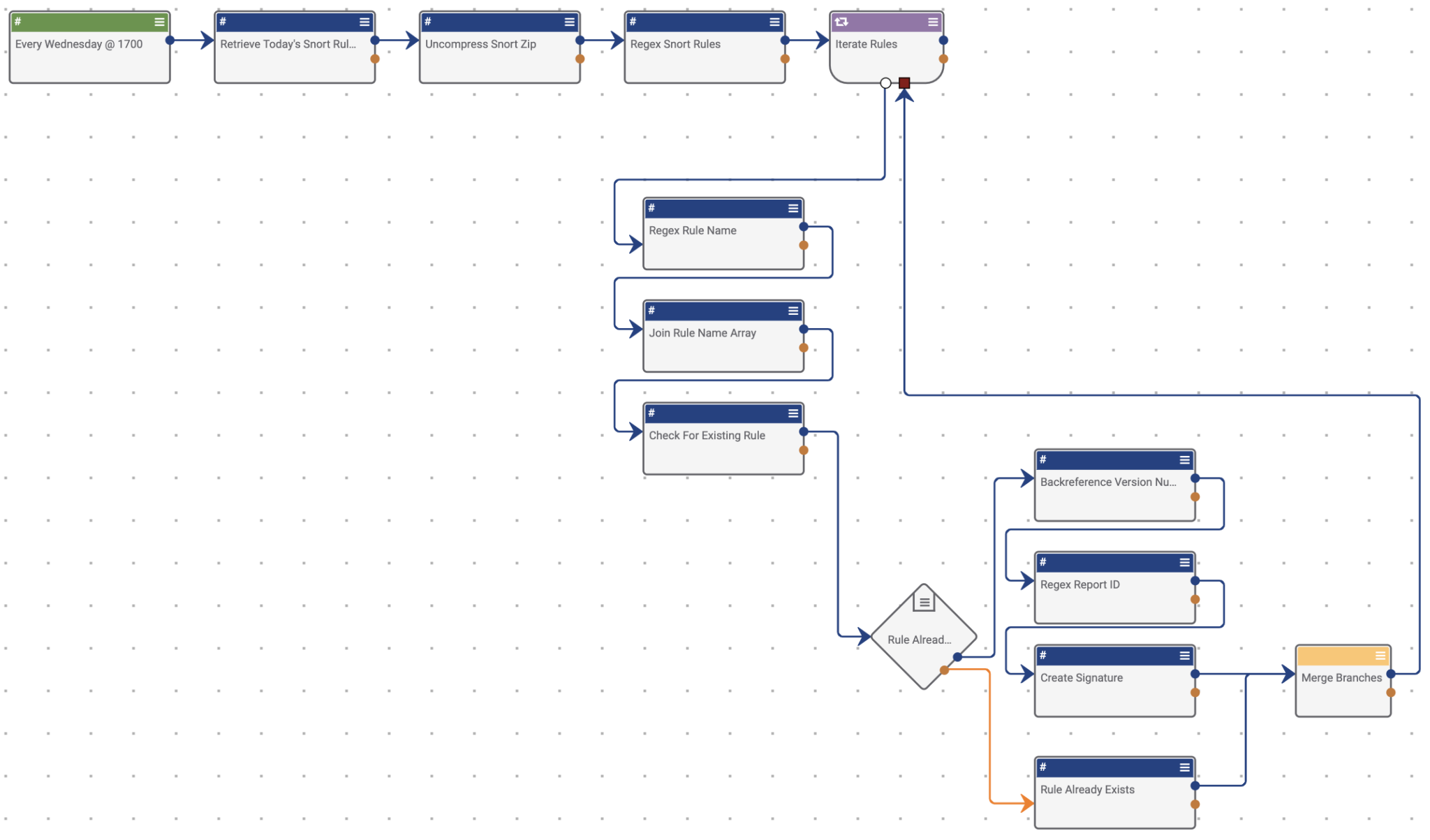
Without Playbooks, you would either have to manually go and download the rules, extract them, split them into individual rules files, and upload each one into ThreatConnect. If you are skilled in Python, you could write code to perform this. But, this Playbook allows you — without writing code — to automate the ingestion of Snort rules into the ThreatConnect Platform for use during investigations as well as automatic deployment of the rules, if you want. This Playbook solves the problem of manually having to retrieve Snort rules from CrowdStrike’s Falcon Intelligence Rules API and memorialize/operationalize them via the ThreatConnect Platform.
The Playbook reaches out to CrowdStrike’s API on a weekly basis, downloads the latest ruleset updates, extracts the rules, then iterates through each one extracting vital information such as the rule name, rule version, etc., and creates them as Signatures in the ThreatConnect Platform. A timed trigger is set to run once a week on Wednesdays at 15:00, but you can change the trigger to whatever they want depending on their needs. And, no out of the box integrations are used; the “integration” was built manually using the HTTP Client to perform the necessary API calls.
To set up this Playbook, you will need to define your CrowdStrike Falcon Intelligence API credentials during the import process. Once the Playbook is imported, the only other configuration that will need to happen is that the desired data owner to be used to storing all of the Snort rules will need to be defined in the following steps:
- Check For Existing Rule
- Create Signature